A social engineering technique used in tricking the users and organizations to provide their sensitive data, such as passwords, usernames, and banking information. Phishing is taken from the fish word because it fishes information that attackers are craving to get. Nowadays, phishing is happening through multiple mediums, such as emails, phone calls, text messages, or QR-codes, which is why companies are losing a lot of money and attackers are exposing millions of data on the internet.
Table of Contents
- How Phishing Works?
- What are the types of phishing
- How To Prevent Phishing?
- Phishing awareness training with Securitywalay
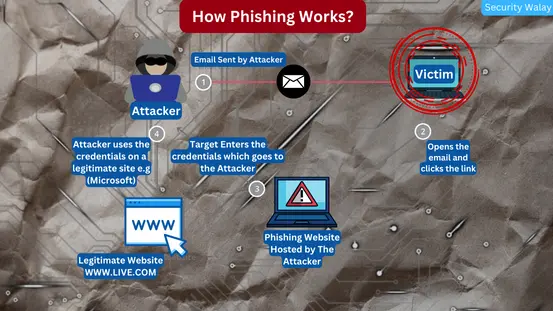
How Phishing Works?
Consider the following scenario: a smooth-talking con artist approaches a group of visitors on a busy street. They strike up a discussion with a warm smile, acting as a helpful local. The scam artist masterfully distracts the tourists with stories and questions, keeping them completely unaware about their wallets and purses are slowly falling into the thief’s hands. In this situation, the simplest approach to perform the “robbery” is to convince the victims that they are not being robbed at all, with charm and diversion serving as the perfect cover.
Cybercriminals design fraudulent messages that look to come from reliable sources such as banks or respected companies in a phishing email. These emails frequently contain urgent or compelling material, asking recipients to act quickly or reveal sensitive information, such as login passwords or personal information. Cybercriminals distract recipients from the reality that they are being targeted for theft by using official-looking designs, psychological methods, and social engineering. The email’s success is based on convincing victims that they are not under attack, all while their vital information is being stolen, similar to a real-world heist in which the victims are unaware that the crime is taking place right in front of their eyes.
The attacker will be creating an urgency that will trick the target into clicking or behaving as they say in the message without them thinking about a second option in analyzing the email, whether it seems suspicious to them.
What are the types of phishing
Email phishing: Almost all phishing attacks are sent using emails to act as a legitimate company to send various requests to the target. They use fake domains by mimicking legitimate ones, such as usbank.com (Legitimate) to usbank.1.com (Fake).
phishing emails have the following objectives to achieve through their target:
- Malicious link to install malware.
- Fake website to harvest the sensitive information.
- A reply with personal information
Spear Phishing: This is also sent via email, but in this type of attack, the attacker has some information about the target, such as his/her name, D.O.B., or phone number.
Smishing: It is an attack that targets the individual through cell phones; this includes SMS messages that are fraudulent or sending fraudulent messages through communication applications such as What‘s App.
Vishing: The target receives a call from the attacker acting as the bank representative to take information about their credit card or from an automated voice acting as the legitimate company; for example, any fraudulent activity through voice is called vishing.
Angler Phishing: A social media account holder acting as a real organization by giving them discounts is called angler phishing.
Pop-up phishing: when a target gets a popup abut their phone is at risk, mostly in Android or Apple, leading them to a malicious link that could compromise the individual’s data.
Whaling: Those who hold higher positions in an organization or are executives of a committee are targeted through this attack, which tries to take information that will compromise the whole network of a company or cause a huge financial loss.
Quishing: Targeted individuals are tricked into scanning a malicious QR code (“50% discount, avail now by scanning”) to get redirected to a website hosted by the attacker, which is an example of a quishing attack. These are either delivered to the inboxes of individuals or left in public places.
Characteristics of phishing email
Too Good to Be True: If there is a statement that grabs your attention, be cautios, because they will tell you sometimes that you won an iPhone, which you didn’t. Be careful of those emails that appear too good to be true!
Attachments: Not every attachment is a legitimate file; attackers often include a malicious file in the email.
Hyperlinks: If you want to read the URL, just hover on the link; you will be able to read it and will know where it might take you. If you are not sure, just visit their actual site and match it with the received link.
Hyperlinks: If you want to read the URL, just hover on the link; you will be able to read it and will know where it might take you. If you are not sure, just visit their actual site and match it with the received link.
Unusual Activity: If you think that your inbox was not expecting the message from a known or unknown sender, do not click it. or from someone you don’t know.
How To Prevent Phishing?
Be vigilant and aware of messages that are spoofed. Securitywalay has instructions for you to be able to defend yourself against phishing.
- Complex Password: Until now, there have been admin accounts that have ‘admin’ as the password. Using a difficult one will prevent the attacker to steal your account.
- Multi-Factor Authentication: If you wan to add extra layer of security and prevent hackers from stealing your data, then use one more factor with your password such as fingerprint, or OTP (One-Time Password).
- Awareness campaigns: All the companies should provide periodical awareness training to the employees and conduct phishing campaigns. By doing so, the employees will be able to use emails securely.
- Periodic Password Changes: Regularly updating your password is a proactive approach that adds extra security. It not only stops the attackers from guessing your password but also significantly delays their progress in trying to find the correct one.”
Phishing awareness training with Securitywalay
To strengthen your organization’s cybersecurity defenses, SecurityWalay provides complete staff awareness training and phishing attack simulations. Our customized training provide your employees with the knowledge and skills they need to identify and respond to possible risks, ensuring they remain attentive against cyberattacks. We deliver real-world scenarios through simulated phish attacks that assist staff train their defense mechanisms, to improve your organization’s overall security posture. You can Contact Us for more Information.



