Cyber Security is the definition of protecting the digital assets of an organization or an individual. Cyber Security attacks include password attacks, malware attacks, Distributed Denial of Service attacks, phishing attacks, SQL injection attacks and so on. Attackers are enchanting their techniques of hacking and targeting sophisticated networks that are deployed in the organization. To ensure the security of assets such as employees or devices, defined standards, frameworks, and good practices in cybersecurity should be in place.
Table of Contents
- What are the categories of cyber security?
- What Are The Most Common Cyber Security Threats?
- What are the advantages of Cyber Security?
- CIA Triad
- What are best practices of cyber security?
What are the categories of cyber security?
- Network Security: Network security is the practice of keeping the computer network secure from cyberthreats.
- Information Security: It is the protection of privacy and data, either in-rest, transit, or in use.
- Operational Security: This includes data storage, processing, handling, and protection. Also, user roles when accessing specific areas of the network or applications.
- Application Security: All the applications have to be free of malicious actors and threats. Sensitive data can be exposed if programs are compromised.
- Security Awareness: People are considered the weakest link in cybersecurity. An accidental click can ruin the reputation of the whole organization or cause incidents that will interrupt the operations of the IT system. Renowned practices of cybersecurity will teach the user how to use emails securely and all the lessons that are required to be cybersecurity aware. Securitywalay offers comprehensive cybersecurity awareness training for organizations and individuals. Contact Us to learn more about SecurityWalay services.
- Mobile Security: from mini to huge tasks are completed using mobile devices such as tablets and cell phones. These devices should be protected from unwanted programs and malicious actors.
- Cloud Security: This security is related to cloud applications and architectures for organizations that use cloud platforms such as Google, Azure, etc.
What Are The Most Common Cyber Security Threats?
Any malicious activity that indicates to a harmful activity such as unauthorized access or the execution of malicious software on a digital device such as a computer, server, mobile device, etc. is defined as a cyber crime and a threat to individuals and organizations. Following are the most common cybersecurity threats described:
Ransomware
This type of attack happens when the user executes the malicious file and it encrypts the sensitive data on the device, then the attacker asks for a financial reward in order to decrypt those files. It is considered a dominant malware that has been developed rapidly in recent years.
Malware
Any program that is intended to harm the user or organization, such as stealing sensitive data or harming the device, is defined as malware. Ransomware, spyware, worms, and viruses are considered types of malware.
Adware
These are advertising software that provide ads to the user based on the stolen data from the user’s machine without their permission.
Man-in-the-middle-attack
This attack happens when an adversary sits between two nodes and listens to legitimate traffic.
SQL Injection
Inserting harmful code into the server of Structured Query language (SQL).
Phishing
Phishing is used by hackers that trick users through a medium, such as email, etc., to harm the device or steal sensitive data.
Denial of Service (DOS)
DoS or Distributed Denial of Service (DDoS) is a term where attackers take any running online service into denial using flood attacks. Overwhelming the network is the method. For example, the hackers send unlimited “handshakes” until the network is not able to handle them anymore and it goes into a “denial” state.
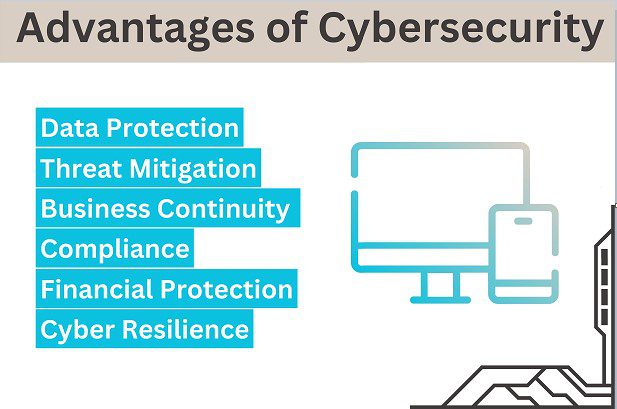
What are the advantages of Cyber Security?
In today’s world, this industry is focusing on the protection of devices and systems. With skilled personnel and competent cybersecurity solutions, they are able to keep websites (or any digital assets) from being attacked by hackers. Professionals’ advice, tips, and best practices are enhancing this field, and the digital world is being secured. A heavy cybersecurity defense mechanism is essential to defend against modern threats and vulnerabilities; without it, the chaos would be appealing.
CIA Triad
There are three main principles used in the security of an organization. Confidentiality, integrity, and availability—these called the CIA—are considered the standards of computer security.
- Confidentiality: Access to assets should be given to authorized personnel.
- Integrity: Modification of sensitive data should be completed by authorized personnel.
- Availability: functions, systems, and data should be available at all times according to user roles.
What are best practices of cyber security?
Multi factor or at least two factor authentication usage.
Use of multi factor authentication.
Usage of a difficult passwords.
Scan devices regularly.
Store sensitive data in a secure place.
Security awareness training.
Avoid clicking on links that are not known.



