-
Darkzero HTB Writeup
nxc smb 10.10.11.89 -u ‘john.w’ -p ‘RFulUtONCOL!’ –generate-hosts-file /etc/hosts Command: nmap -T4 -A -v -Pn 10.10.11.89 Command: smbclient //10.10.11.89/SYSVOL -U…
-

(破解盒子) Imagery
Season 9 HTB HTB Season 9 — titled GACHA — is the latest competitive hacking season from Hack The Box…
-
The Tunnel Without Walls — HTB
Running Basic Analysis Process Listing python3 vol.py -f memory_dump.lime linux.pslist.PsListFinding Hidden Processes python3 vol.py -f memory_dump.lime linux.pstree.PsTreeExtracting Bash History python3 vol.py -f memory_dump.lime…
-

Top 7 Breaches That Could Compromise Your Endpoint Security
In today’s hyper-connected world, endpoint security is a cornerstone of any robust cybersecurity strategy. With the proliferation of devices—laptops, smartphones,…
-

Top 8 Continuous Security Monitoring Tools for better Cybersecurity Defense in 2025
Introduction In an era where cyber threats evolve at an unprecedented pace, organizations must prioritize robust cybersecurity defenses to protect…
-
3 Templates for Creating Effective Security Advisories for Cybersecurity Teams
Introduction Security advisories are essential communications that inform stakeholders (IT teams, developers, executives) about vulnerabilities, threats, and recommended actions. A…
-
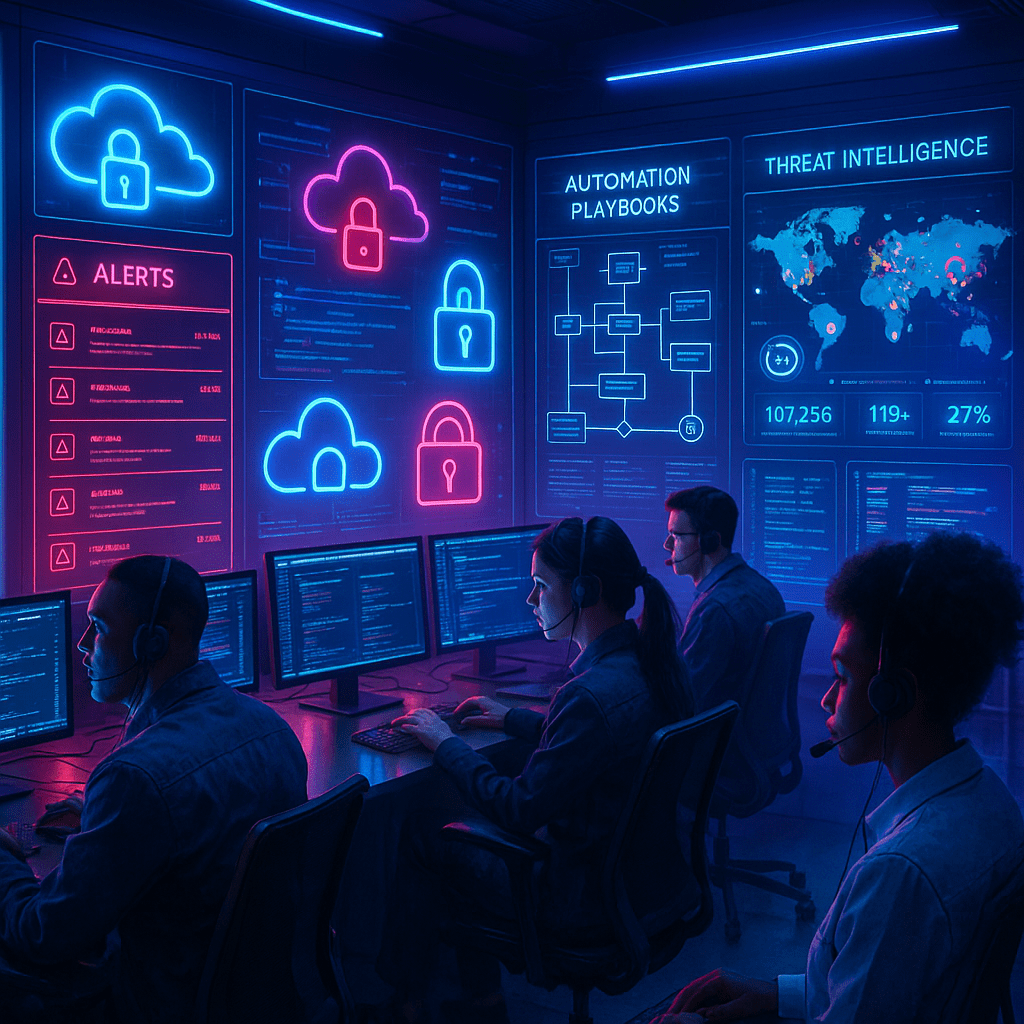
Security Orchestration, Automation and Response (SOAR) Solutions. (2025)
Guide for security teams to detect, respond, and adapt faster 1. Introduction In today’s cybersecurity landscape, alert fatigue has become…

