Zero Trust Security is the practice of not trusting any connection in the network even those who are inside the network; there is connection but the only difference is that it requires continued identification in the private network, whether it is a device or a user trying to access a resource, even if it was disconnected within seconds from the resources, such as a VPN. In this blog post we will talking about the Principles, advantages and disadvantages of Zero-Trust Security.
Table of Contents
- Introduction
- The main principles behind Zero Trust, what are they?
- Advantages of Zero-Trust Security
- Disadvantages of Zero-Trust Security
- In Conclusion

Introduction
Zero-Trust security means that any resource is a no trust entity from inside or outside the network, and the methodology of verification is a requirement from anyone of anything trying to gain access to resources on the network. Also, studies shows that the average cost of single data breach has crossed over $3 Million. based on the number, most of the companies are planing to implement Zero-trust architecture by 2025.
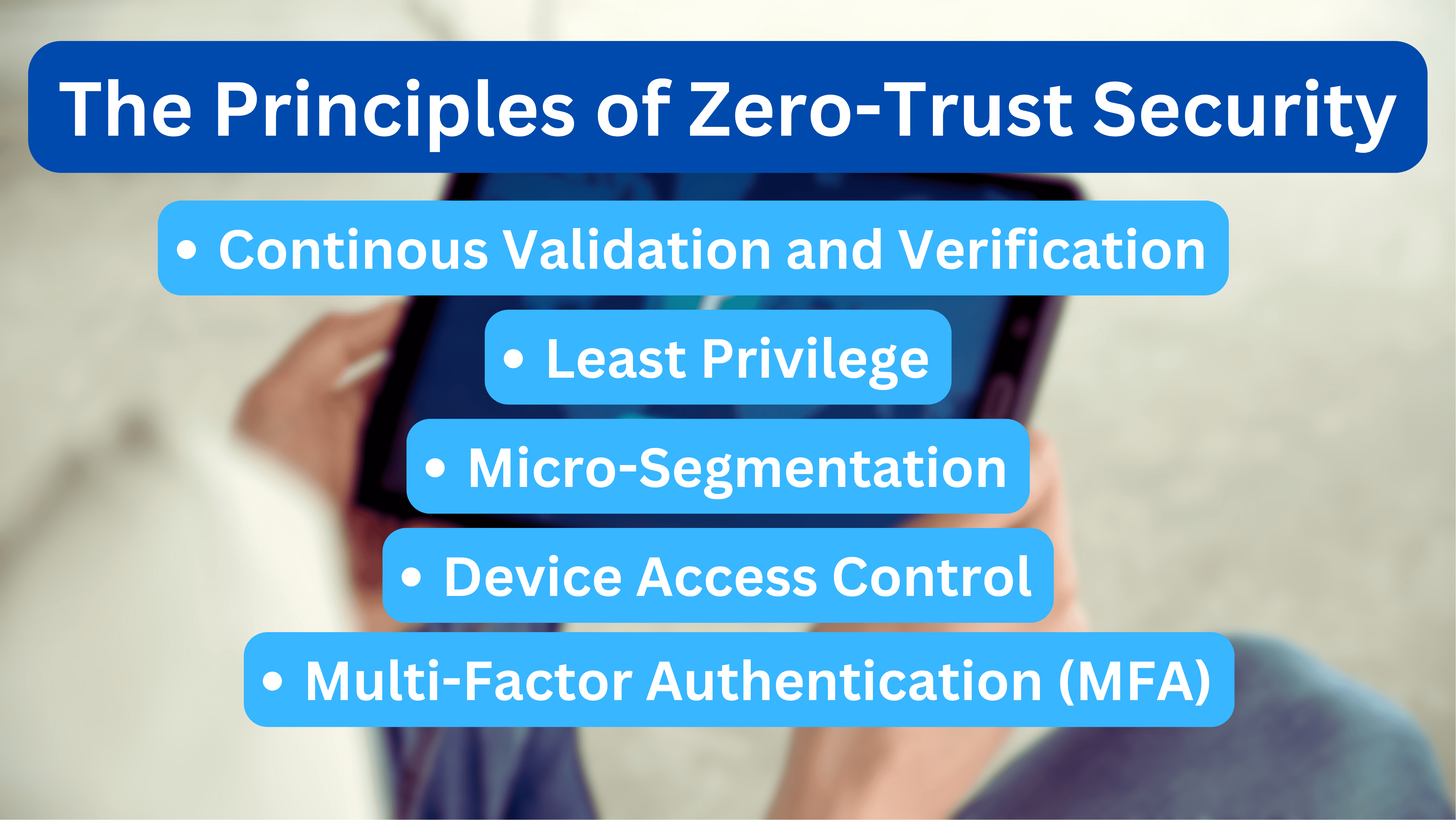
The main principles behind Zero Trust, what are they?
Continuous Validation and monitoring
The main idea of a zero-trust network assumes that there are attackers internally and externally on the network, which means that no devices or users are trusted automatically. The user’s identity and privileges are re-validated once the connection reaches its timeout, forcing the devices and user to be verified on a regular basis.
Microsegmentation
Zero-trust networks use the micro-segmentation technique, which is the practice of breaking up security segments into tiny zines to provide separate access to different parts of the network. A VLAN would be an example of micro-segmentation, as a user can access only one zone and will not be able to access any other zone without separate authorization. However, micro-segmentation is more than just VLANs; it is about generating separated segments with unique access controls for increased security.
Least Privilege
Least Privilege Access is another principle of the Zero Trust security model. It means that the access given to users is only limited to their needs, like a marketing department can only access several applications. This will reduce the activity in the sensitive area of the network.
Device Access Control
Device access control is the diligent guardian in the world of Zero Trust security, demanding confirmation of identification, level of security, and authorization from each device seeking an entry. It is a strong protector of digital assets, ensuring that trust is acquired rather than assumed. In this approach, the network is an unbreakable fortress, with each device’s access strictly controlled, protecting your data from the onslaught of cyber threats.
Multi-Factor Authentication
it is one of the main principles of zero trust security. Multi factor authentication means that one or more credential is needed when a users authenticates; just by using one factor such as password is not enough any more in this new digital era. Take an example of Facebook and Google when the user enters the password, an automated code is sent to the device in order to enter as the second evidence.
Advantages of Zero-Trust Security
- Improved Visibility and Control: This model gives businesses an in-depth picture of network activity, allowing them to track who accesses what information, when, and from where. This degree of protection is critical for recognizing unusual activity quickly and mitigating breaches of information and cyber attacks.
- Enhanced Security: Zero Trust security improves security by restricting access to just those who need to know, minimizing the attack surface, and making it more difficult for potential intruders to get unauthorized access.
- Insider Threat Mitigation: Implementing strong access controls for all users, no matter what position they hold. Potential damage can be contained regardless of whether an insider’s credentials are affected.
Disadvantages of Zero-Trust Security
- Tough Implementation: Zero Trust implementation can be hard and time-consuming, necessitating careful planning, collaboration, and investment in new technology.
- Expensive Charges: Implementing Zero Trust can be expensive, requiring investments in latest innovations, personnel training, and continuous maintenance.
- User Experience: Due to the additional authentication procedures necessary to access resources, Zero Trust may result in a less seamless user experience.
In Conclusion
Zero-trust security is more than a term; it is a requirement in today’s ever-changing digital landscape. It calls into question established trust paradigms by mandating constant verification for all users and devices. This strong framework, which emphasizes Continuous Validation, Microsegmentation, Least Privilege, Device Access Control, and Multi-Factor Authentication, provides improved security, visibility, and insider threat prevention.
As the price of breaches of information rises, corporations swiftly adopt the Zero Trust strategy, with plans to execute it by 2025. Zero trust is more than a security concept; it is a dynamic phenomenon that protects your digital domain in an untrustworthy environment. Remember the power of Zero Trust when evaluating network security—it’s your shield in a Zero Trust world, preserving your digital future.

