In today’s era of technology, where the Internet of Things (IoT) has become so much in use, it has given the benefits to the industry and to the daily life’s of individuals. Due to the inter-connectivity of these devices, it exposes them publicly to the intranet which makes it the easy target for the adversaries to exploit vulnerabilities and weaknesses. Cybersecurity has become one of the major concerns for the vendors and individuals who produce such devices or provide services in this area. In this blog post, I have written the seven key differences between IoT and cybersecurity, I was able to explore solutions to address the challenges which we’re facing in this century to ensure the security and privacy of IoT systems.
Table of Contents
- Understanding IoT
- Exploring the Benefits of IoT
- Key Characteristics of IoT
- Examples of IoT Devices
- IoT Cybersecurity Challenges
- Mitigating these Risks:
- Overview of Cybersecurity
- Key Differences between IoT and Cybersecurity
- The Role of Standards and Regulations
- Emerging Technologies for IoT Security
- The Future of IoT and Cybersecurity
- Conclusion
Understanding IoT
The Internet of Things (IoT) is a term used to describe a network of interconnected physical devices, objects, and systems that have the ability to collect and exchange data. This network includes many devices such as smartphones, wearable gadgets, home appliances, industrial machinery, and more. These devices are equipped with sensors and actuators that enable them to interact with the physical environment and communicate with each other via networks.
Exploring the Benefits of IoT
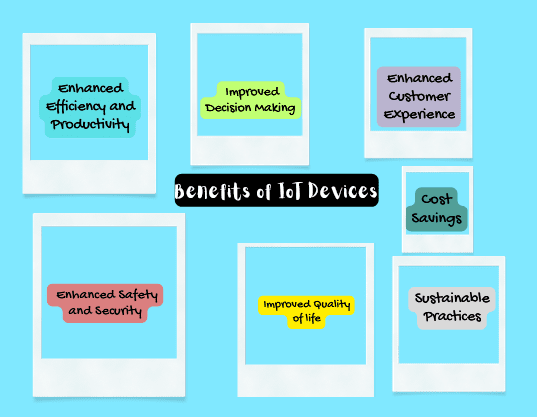
The Internet of Things (IoT) offers various benefits to different sectors such as retail, agriculture, automotive, and etc. The connectivity of these devices through the exchange of data changes the way we live and work. following are some of the benefits of IoT:

IoT enables automation and optimization of processes, which increase the efficiency and productivity of sectors who are using it. For example, in manufacturing, IoT sensors can monitor equipment performance in real-time, allowing for predictive maintenance and reducing downtime.
IoT generates lots of data that can be analyzed to gain valuable insights. This data-driven decision can make the best choices, optimized operations, and deliver better products and services, and that helps the business to grow in the right needed steps.


IoT presents cost-saving opportunities through various means. For instance, in agriculture, IoT-based smart irrigation systems deliver water precisely where and when it is needed, minimizing water waste and reducing costs as an example.
IoT facilitates the implementation of advanced security and surveillance systems. Smart home devices, for example, enable homeowners to remotely monitor their property, detect intrusions, and receive real-time alerts.


IoT innovations enhance the quality of life for individuals. Connected healthcare devices enable remote patient monitoring, allowing for timely interventions and personalized care. Smart home technologies provide convenience and comfort, automating tasks to better living experiences. nowadays, an individual can drive the car from parking to his destination remotely including the remote engine start while at home.
IoT contributes to sustainability efforts by enabling efficient resource management. In energy management, IoT devices can minimize the energy consumption, monitor the sources of renewable energy, and reduce carbon footprints.


IoT contributes to sustainability efforts by enabling efficient resource management. In energy management, IoT devices can minimize the energy consumption, monitor the sources of renewable energy, and reduce carbon footprints.
Key Characteristics of IoT
IoT devices are characterized by their ability to sense and collect data, communicate with other devices or systems, and make intelligent decisions based on the collected data. They often rely on wireless connectivity, such as Wi-Fi or Bluetooth, to connect to the internet and exchange information.
Examples of IoT Devices
IoT devices have become increasingly prevalent in our daily lives, offering convenience, efficiency, and connectivity. Here are some notable examples of IoT devices across different domains:
1. Smart home devices
Smart home devices have gained popularity, allowing homeowners to control various aspects of their homes remotely. Examples include smart thermostats, which enable temperature control via mobile apps, and smart security systems with motion sensors and video surveillance.
2. Wearable IoT devices
Wearable IoT devices, such as fitness trackers and smartwatches, have revolutionized personal health monitoring. These devices track physical activities, monitor heart rate, sleep patterns, and provide real-time health insights.
3. Connected Cars
IoT technology has transformed the automotive industry with connected cars. These vehicles use sensors and internet connectivity to offer features like GPS navigation, remote control, driver assistance systems, and real-time vehicle diagnostics.
4. Industrial Iot IIoT
IIoT devices are deployed in industrial settings to optimize operations, improve efficiency, and enhance safety. Examples include sensor-equipped machinery that can monitor performance, predictive maintenance systems that detect equipment failures in advance, and inventory management systems that automate supply chain processes.
IoT Cybersecurity Challenges
As the Internet of Things (IoT) continues to grow, it brings with it unique cybersecurity risks and vulnerabilities that need to be understood and addressed accordingly. Let us look at some significant areas of concern:
1. Weak Authentication
Many IoT devices have weak authentication methods, such as easily guessable passwords. This enables illegal access to these devices easy for attackers.
2. Lack of Encryption
Insufficient or improper encryption of data transmitted by IoT devices and networks can expose sensitive information to unauthorized access and exploitation.
3. Insecure Frimware
IoT devices often have vulnerabilities in their firmware, which can be exploited by hackers. Failure to update firmware regularly leaves devices open to known vulnerabilities.
5. Privacy Breaches
IoT devices collect and transmit a large amount of personal and sensitive data. Unauthorized access to this data can result in privacy breaches and compromise individuals’ personal information.
6. Data Theft
IoT devices collect and transmit a large amount of personal and sensitive data. Unauthorized access to this data can result in privacy breaches and compromise individuals’ personal information.
7. Disruption of Critical Infrastructure
With IoT devices being integrated into critical infrastructure systems like power grids and transportation networks, compromising these devices can lead to significant disruptions and safety hazards.
Mitigating these Risks:
To address these risks and enhance IoT security, we can take the following measures:
1. Strengthen Authentication
Implement strong authentication methods, such as using complex passwords and multi-factor authentication, to prevent unauthorized access.
2. Robust Encryption
Ensure that data transmitted by IoT devices is properly encrypted to protect it from unauthorized interception.
3. Regular Firmware Update
Manufacturers should provide regular firmware updates to address vulnerabilities and improve device security.
4. Effective Device Management
Practice proper device management by regularly updating software, configuring security settings, and monitoring device activity.
5. Privacy by Design
Incorporate privacy protection measures into the design and development of IoT devices to safeguard user data.
6. Security Awareness and Education
Promote cybersecurity awareness among users and educate them about best practices for securing IoT devices
Overview of Cybersecurity
Cybersecurity is important in the current digital era to give protection of our computer systems, networks, and data from intrusion, threats, and weaknesses. Let’s investigate the main features of cybersecurity:
Definition
The practices and precautions taken to protect computer systems, networks, and data against online attacks are collectively referred to as cybersecurity. Defending against unauthorized access, data breaches, malware, and other criminal activity is part of this.
Significance
Cybersecurity is essential in a networked world to protect the privacy, availability, and integrity of data. It is the protection against financial loss and reputational harm and helps stop unauthorized individuals or abnormal entities from compromising important information.
Proactive Measures
A variety of recommendations are used to improve the overall cybersecurity. Strong access controls, data encryption, the use of firewalls and intrusion detection systems, and frequent vulnerability assessments are a few of these.
Threat Landscape
New threats are continuously emerging, and the cybersecurity landscape is no exception. Malware, phishing scams, ransomware, and social engineering are some of these risks. By putting in place proactive procedures to find, stop, and react to possible security breaches, cybersecurity addresses these dangers.
Incident Response
Despite precautions, security mishaps can still happen. The process of quickly locating, containing, looking into, and recovering from security issues is known as incident response. It entails reducing the impact, protecting the evidence, and promptly returning to normal operations.
Continuous Monitoring and Adaption
As an ongoing endeavor, cybersecurity calls for constant observation and adjustment. Software upgrades, patch management, and regular security audits all aid in locating vulnerabilities and addressing them quickly. In order to keep one step ahead of hackers, it is essential to stay educated about new threats and developing technology.
Compliance and Regulations
Keeping cybersecurity in tact requires adherence to industry-specific standards and laws. To protect sensitive information, organizations must follow legal requirements such data protection regulations and put in place the necessary security measures.
Key Differences between IoT and Cybersecurity
Connectivity and Complexity
- IoT devices are interconnected, creating a complex network that poses challenges for cybersecurity.
- The large number of devices and their diverse capabilities make it difficult to apply traditional cybersecurity methods.
- Specialized approaches are needed to manage the complexity and ensure secure communication among IoT devices.
Data Volume and Privacy
- IoT devices generate vast amounts of data, including personal and sensitive information.
- Protecting the privacy and confidentiality of this data is crucial.
- Robust data protection measures, such as encryption and data anonymization, are necessary to safeguard sensitive information.
Device Heterogeneity and Standardization
- IoT devices come in various types with different capabilities, protocols, and security standards.
- Ensuring a consistent and robust security posture across diverse devices is a challenge.
- Standardization efforts aim to establish common frameworks and security guidelines for IoT devices.
Distributed Architecture and Network Security
- IoT operates on a distributed architecture, with devices spread across different networks and environments.
- Traditional perimeter-based security is insufficient for protecting IoT devices.
- Layered security measures, such as secure communication protocols and access controls, are needed to secure IoT networks.
Resources Limitation and Patch Management
- Many IoT devices have limited resources like processing power and memory.
- Applying security patches and updates can be challenging due to these limitations.
- Effective patch management strategies and remote update capabilities are essential for addressing vulnerabilities in IoT devices.
Lack of Security by Design
- Some IoT devices have been developed without sufficient security considerations.
- This lack of security by design leaves devices vulnerable to attacks.
- Emphasizing security from the early stages of device development is crucial to ensure inherent security.
Evolving Threat Landscape and Adaptive Security
- The threat landscape for IoT is constantly evolving, with cybercriminals targeting IoT devices.
- Continuous monitoring, threat intelligence, and adaptive security strategies are necessary.
- Keeping up with emerging threats and implementing proactive security measures is essential for IoT security.
The Role of Standards and Regulations
Industry standards and regulations play a crucial role in addressing the security challenges associated with IoT devices. They provide guidelines and frameworks that help establish best practices and ensure a common baseline for security across different IoT ecosystems. Here are some notable standards organizations and regulations governing IoT security:
National Institute of Standards and Technology (NIST)
- NIST has developed a comprehensive set of guidelines and cybersecurity standards specifically tailored for IoT devices and systems.
- Their guidelines focus on areas such as device identification, secure firmware updates, and network security.
- NIST’s recommendations serve as a valuable resource for organizations and manufacturers to enhance the security of their IoT deployments.
European Union Agency for Cybersecurity (ENISA)
- ENISA plays a significant role in promoting cybersecurity across the European Union, including IoT security.
- They provide guidance and best practices for securing IoT devices and networks, addressing areas such as risk assessment, threat intelligence, and incident response.
- ENISA’s efforts contribute to the harmonization of IoT security practices within the EU.
General Data Protection Regulation (GDPR)
- GDPR is a landmark regulation introduced by the European Union to protect the privacy and data rights of individuals.
- Although not specific to IoT, GDPR has implications for IoT security due to the sensitive nature of personal data collected by IoT devices.
- The regulation imposes strict requirements on organizations handling personal data, including the need for explicit user consent and robust security measures.
Emerging Technologies for IoT Security
As the complexity and scale of IoT deployments increase, innovative technologies are being explored to enhance IoT security. These technologies offer advanced capabilities that can help mitigate cybersecurity threats and protect IoT devices and networks. Here are some emerging technologies for IoT security
Machine Learning
As the complexity and scale of IoT deployments increase, innovative technologies are being explored to enhance IoT security. These technologies offer advanced capabilities that can help mitigate cybersecurity threats and protect IoT devices and networks. Here are some emerging technologies for IoT security
Blockchain
Blockchain technology offers a decentralized and tamper-proof platform for secure data exchange and storage. Its immutability and cryptographic features make it suitable for securing IoT transactions and ensuring data integrity. By leveraging blockchain, IoT devices can securely record and verify data exchanges, making it difficult for unauthorized parties to manipulate or tamper with the information. This technology holds promise in enhancing the trust, transparency, and security of IoT ecosystems.
Anomaly Detection
Anomaly detection techniques utilize statistical analysis and machine learning algorithms to identify deviations from normal behavior within IoT networks. By establishing baseline patterns of expected behavior, any unusual activities or deviations can be flagged as potential security incidents. Anomaly detection plays a vital role in identifying and mitigating both known and unknown threats, enabling rapid response and minimizing potential damage.
Artificial Intelligence and Automation
Artificial intelligence (AI) and automation have transformative potential in IoT security. AI-powered systems can continuously monitor and analyze vast amounts of IoT data, identifying patterns and anomalies that may indicate security risks. Automation can enable swift responses to security incidents, such as initiating incident response procedures or isolating compromised devices. By combining AI and automation, organizations can enhance threat detection, response times, and overall security effectiveness in the dynamic IoT environment.
The Future of IoT and Cybersecurity
The future of IoT and cybersecurity is marked by rapid advancements and evolving challenges. As technology continues to progress, here are some insights into the future trends and developments in the IoT and cybersecurity landscape
1. Increased Connectivity and Integration
The IoT ecosystem is expected to expand further, with more devices becoming interconnected and integrated into various aspects of our lives. This increased connectivity brings convenience and efficiency but also introduces additional security risks. As IoT devices become more intertwined with critical infrastructure, industries, and personal lives, robust security measures and frameworks must be in place to safeguard against cyber threats.
2. AI & ML
Artificial intelligence (AI) and machine learning (ML) will play significant roles in the future of IoT and cybersecurity. AI and ML algorithms can analyze vast amounts of data generated by IoT devices, detect patterns, and identify potential security threats in real-time. These technologies can enhance threat detection, response, and even automate security processes to adapt to evolving threats.
3. Collaborative Approach
Addressing the complex cybersecurity challenges of IoT requires collaboration among various stakeholders, including industry, government, and academia. Collaboration is crucial to establish best practices, share threat intelligence, develop standardized security frameworks, and promote awareness and education around IoT security. By working together, stakeholders can leverage their expertise and resources to build a secure IoT ecosystem.
4. Data and Privacy Protection
As IoT devices gather and transmit sensitive data, privacy and data protection will become increasingly important. Stricter regulations and standards are expected to emerge to govern the collection, storage, and usage of IoT data. Ensuring the privacy of individuals and implementing robust data protection measures will be crucial in maintaining user trust and addressing privacy concerns associated with IoT deployments.
5. Cybersecurity Skills and workforce
The demand for cybersecurity professionals with expertise in IoT will continue to rise. As IoT expands, organizations will require skilled individuals who can understand the unique challenges and develop effective security strategies for IoT deployments. Investing in cybersecurity education and training programs will be essential to bridge the skills gap and foster a capable workforce to protect IoT devices and networks.
Conclusion
In conclusion, it is imperative to acknowledge and address the cybersecurity challenges within the rapidly expanding IoT landscape. Prioritizing the implementation of robust security measures and staying well-informed about IoT security best practices is crucial for organizations and individuals. Advocating for stronger security measures and supporting industry standards and regulations are key to safeguarding IoT ecosystems. Collaboration among stakeholders, including industry, government, and academia, is essential to establish a comprehensive framework for IoT security. By taking proactive measures and remaining vigilant, we can unlock the full potential of IoT while ensuring the integrity and security of our interconnected world. Let us strive for a future where innovation and safety coexist harmoniously.