our services
Business-First Security Solutions That Fits Your Needs
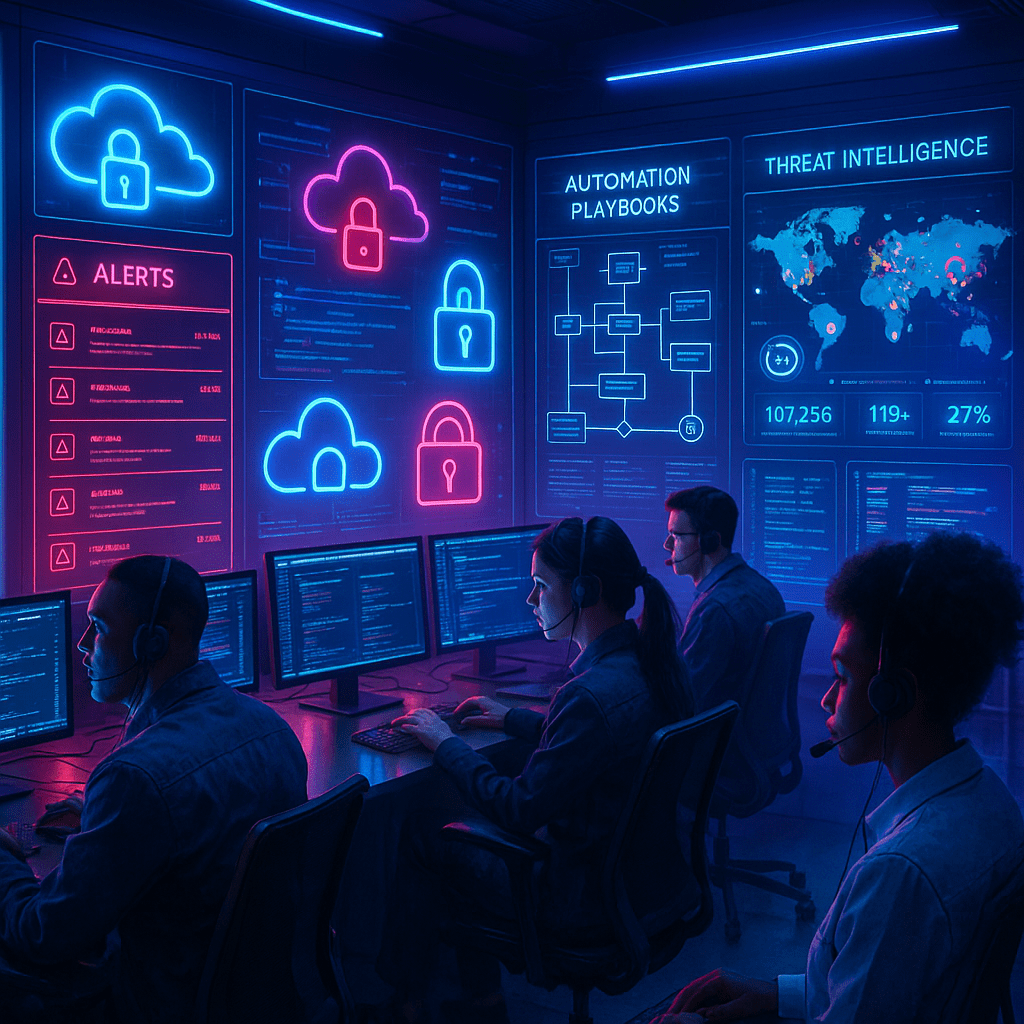
Security Operation Center
Our Managed SOC provides continuous monitoring, detection, and incident response services using advanced SIEM, threat intel, and expert analysts. Whether fully managed or hybrid, we help organizations reduce dwell time and meet critical compliance needs like NIST CSF, ISO 27001, and CIS Controls.
Info-sec Security Awareness
Your employees are the first line of defense. We deliver customized, role-based security awareness programs designed to change behavior, reduce risk, and meet compliance requirements (ISO 27001, HIPAA, PCI, etc.). Available as onboarding modules, live sessions, or LMS-ready content.
Resource As a Service
We provide skilled cybersecurity professionals as an extension of your internal team — available on a project-based or long-term basis. Whether you need a SOC analyst, compliance lead, or a virtual CISO, our experts integrate seamlessly with your environment to strengthen security capabilities without long-term overhead.
Penetration Testing & Vulnerability Management
We perform internal, external, and application-layer penetration testing to identify exploitable vulnerabilities — before attackers do. Our reports are detailed, actionable, and aligned with compliance frameworks like OWASP, PCI DSS, and MITRE ATT&CK.
Compliance & Security Risk Assessments
Security without governance leads to audit failure. We help organizations build, revise, and enforce cybersecurity policies, procedures, and control documentation to satisfy auditors and regulators. This includes everything from access control policies to incident response plans.
Audit-Ready Information Security Assessments
We assess your current security posture against leading standards like ISO 27001, NIST CSF, SOC 2, or custom regulatory mandates. Our team identifies gaps, quantifies risk, and delivers a prioritized remediation roadmap — perfect for pre-audit preparation or annual governance reporting.
Our Core Services
- Cyber Security
- Risk Assessment
- Network Security
- Endpoint Monitoring
- Resource as service
- Backup & Recovery
FAQS
What is cyber security and why is it important?
Cybersecurity protects digital systems, networks, and data from theft, damage, or disruption. In 2025, threats like AI-powered phishing, ransomware-as-a-service (RaaS), deepfakes, and supply chain breaches are escalating. Organizations must guard against unauthorized access, preserve data integrity, and maintain business continuity. Effective cybersecurity enables trust, protects reputation, and ensures regulatory compliance with frameworks like ISO 27001 and SOC 2.
How can I protect my personal data online?
Yes, we offer personal cybersecurity consultation to help safeguard your home and family. We cover best practices including strong passwords, multi-factor authentication, secure Wi‑Fi configuration, smart device isolation, and antivirus setup. We’ll help you protect your devices, smart home apps, and online presence using home device posturing and privacy hygiene strategies.
Do you offer 24/7 monitoring?
Yes, through our Managed Detection & Response (MDR) service—part of our SOC offering. We provide continuous threat monitoring, alert triage, and incident response, backed by AI-driven log correlation and human analysts.
Can you prevent ransomware attacks?
Yes—using a layered approach that includes endpoint protection, backups, threat detection, and incident readiness. We deploy EDR tools, test for ransomware readiness, train users, use behavioral analytics, and help plan tabletop exercises. Our combination of preventive controls and readiness strategies helps reduce ransomware damage and recovery time.
Do you provide security audits?
Yes—our Audit-Ready Information Security Assessments evaluate your security posture against industry standards such as NIST CSF, ISO 27001, and SOC 2. We deliver gap analysis, risk registers, maturity scoring, and remediation roadmaps. These audits not only identify vulnerabilities but also prepare you for external audits and regulatory readiness.
Can you train our staff on cyber safety?
Absolutely. Our Information Security Awareness Training is tailored to your workforce—with modules on AI-enhanced phishing, insider threat awareness, password best practices, and device hygiene. We include simulations, phishing campaigns, and compliance tracking to build a proactive security culture and meet audit requirements.
How quickly can you respond to threats?
We guarantee incident response within 30 – 60 minutes, depending on severity. Our integrated SOC and trained analysts use automated playbooks and escalation protocols to contain threats quickly and minimize damage.
How often do you update security measures?
We update your defenses continuously—patching vulnerabilities as they’re discovered, reviewing policies quarterly, and performing annual risk assessments. In 2025, adopting Continuous Exposure Management (CEM) ensures proactive identification and mitigation of security gaps.
How do I know if a website is secure?
Check that the URL begins with “https://”, verify the SSL certificate (click the padlock), review the domain name carefully, and inspect for clear privacy policies. Avoid websites that request sensitive data without proper encryption, or that show mixed content (both HTTP and HTTPS). Use browser-based security tools or plug-ins that flag suspicious sites.
Want to Talk Cybersecurity? We’re All Ears!
We’re confident in the quality, impact, and precision of our services. If you’re not 100% satisfied, we’ll make it right — or your money back. That’s our promise.