Ransomware is the malware which locks access to files, applications, and databases on their system through encryption. Ransom payments are demanded from the organizations as well as individuals. Once payments are made, the keys for decryption are then given by the adversaries. It is also designed to spread on all over the networks and target databases which can make the whole operation hang in a matter of seconds. This type of malware has become the most prominent. Organizations are put in a situation where the easiest way provided by the adversaries to resolve this issue is by paying the ransom.
Table of Contents
- How ransomware works?
- Why ransomware attacks becoming popular?
- What is (RaaS) Ransomware-as-a-Service?
- What forms of Ransomware are there?
- How to protect against ransomware?
- How to Respond to Ransomware Attack?
- FAQs
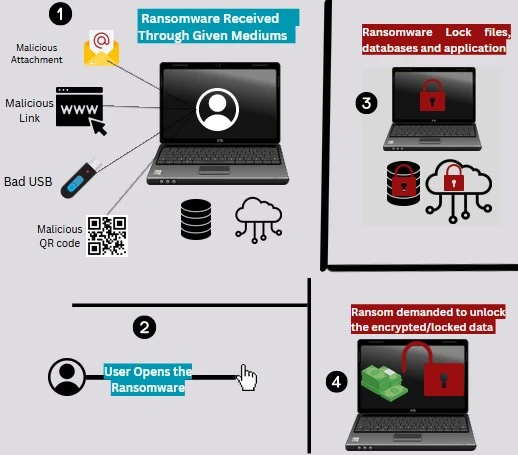
How ransomware works?
Cryptographic method used in ransomware is called encryption. To encrypt or decrypt a file, two pairs of keys are used such as public and private. The adversary stores the private key on his server for the target to use to decrypt the locked files. The attackers make it almost impossible to decrypt those files without the private key. Once the victim pays the ransom, the attacker then provide the keys to the target.
Mostly, the ransomware is delivered through email as well as other mediums sometimes like USB. Now the ransomware (or any malware) needs to enter an endpoint to maintain its presence. Once it is executed successfully, it drops the malicious binaries which search for important doc files, photos, and databases to encrypt.
In most attacks, the adversaries give 24 to 48 hours to pay the ransom in order to decrypt the encrypted files, if such demand is not fulfilled, they give a warning of destroying the valuable data on the system. This happens through a prompt written by the attacker itself and inserted into the system as a “TXT” file or on the dashboard of the malware.
Why ransomware attacks becoming popular?
Ransomware started growing quickly when WannaCry outbreak a huge scaled attack in 2017. Many variants of ransomware developed and innovated as it seemed to be possible and profitable cybercrime. Nowadays, ransomware is easily available on the black market as well. COVID-19 pandemic made a huge contribution to the ransomware criminalized industry. they have compromised 50% more systems in the first Q3 of 2020 in which an increase of 50% attacks were seen.. The attacks has increased 13% more in the previous 5 years.
What is (RaaS) Ransomware-as-a-Service?
It is an economic model related to cybercrime which allows the developers of ransomware to earn money for what they have created without distributing these threats. Those criminals who are considered non-technical buy such malware and pay the developers a small percentage. There are two types of RaaS, either they give you the registration option in order to gain access, or a small amount is required to subscribe to the service.
What forms of Ransomware are there?
There are two categories of ransomware such as crypto and locker ransomware.
- Crypto: Crypto ransomware is when the attacker aims to encrypt the target files.
- Locker: Basic functionality of the computer is affected by Locker ransomware.
- Scareware: Without damaging user’s file, attackers use pop-up technique and flood the user’s screen. Also, a fake anti-virus software is used in scareware which tells the user that their computer is locked and got infected with a virus, they demand for a ransom in order to unlock their system.
Leakware: Attackers warn their target that the stolen data will be public if the ransom is not paid. or they act as law enforcement, illegal activities have been detected, and by paying the ransom, jail time can be avoided, which is how the attackers warn their target.
How to protect against ransomware?
If you want to avoid ransomware to infect your system. the following tips are given for you to consider
- Use of Security Software
-
Use of Security software: Any system connected to the internet has to be protected from viruses and malwares. usage of any leading security software is recommended even if the user is not able to buy the premium version, at least the free version will make sure that you are free from cyber threats. Securitywalay recommends Gatekeeper for Macintosh users, Microsoft defender for Windows User, and CalmAV for Linux users (It’s and Open-source scanner with GUI).
- Email Security Aware
-
Mostly, ransomware and other malwares are delivered through emails, SMS, and other mediums such QR Codes. The user will have to be very careful if the link or an attachment is received from an entity that is unknown or even known and you have suspicion of the link received. Social engineering are used by the attackers as they want you to some how execute the ransomware.
- Back up your data & make it secure
-
Ransomware intent is to lock you out from those files which are valuable to you. one of the effective ways to mitigate the risk of losing such valuable assets is to keep back up of your data. If the ransomware hits an entity, it can still redo the Operating System and download the data from the backup. Note that, not all data can be returned, but trying such solution may partially bring your files back.
- Secure Networks
-
The Internet has become our necessity. Users always in the hunt of free or un-secure wireless connections. To stay secure, users are advised to connect to networks that are known, such Public Wi-Fi networks, as they can be harmful and may damage your data. These can cause ransomware attack, because it is sometimes implemented by these attackers, as you connect to such Wi-Fi, it can install the ransomware into the user’s device without their knowledge.
- Stay Up-To-Date
-
Cybersecurity awareness is important for individuals and organizations as well. non-technical personnel are also required to have at least the minimal knowledge required to stay aware & secure. if you are hit with a ransomware and your data is not backed up, there are some decryption tools that can help you in decrypting your valuable data.
- Security Awareness
-
Awareness of security is an important part where organization have to invest in order to keep their employees safe, secure, & aware. these trainings can make you think before clicking on the unknown links twice. SecurityWalay offers a comprehensive security awareness training for your employees. Contact Us to learn more.
How to Respond to Ransomware Attack?
If you have a suspicion that you have been targeted with Ransomware attack, you will have to act as quick as possible. We will recommend some steps for you to minimize the damage and can make your operations go back to normal as soon as possible.
Isolation
Modern ransomware spread to the whole network, devices and databases once it is executed in one instance such as endpoint or server. this can result in ruining your whole business for good. It is very important to isolate your target device from the network as soon as possible, because it can prevent the spread across the systems and networks.
Check the damages
Once it is confirmed that your device is infected, you will still have to check for files with strange extension names (.ecc, .ccc, .ttt, .xyz, .locked, .crinf, .encrypted) or a personnel having difficulty in opening a file. if there are such files, the system should be isolated until the threat is triaged properly. A list of all the infected devices (databases, network devices, endpoints) has to be made and then checked if the attack is still active, if not then isolation is a must solution to contain.
Decryptors
There are decryptors available which can be used for your locked files. this depends on the ransomware that was executed, if researchers of security have already broke the algorithm of encryption it will be easier for the target organization to recover your files.
Operating System (OS) Tools
Many Operating Systems took the measurement of such attacks specially Windows 10 to the next level by providing built-in recovery tools. Such tools can take your systems back to a previously established point. Modern Malwares are corrupting and disabling these type of application to make it difficult for the user to recover it.
Report to Authorities
It is better to inform authorities once the attack has occurred because ransomware is considered a cybercrime. also, authorities always have the best technologies in place, reporting such attacks can take increase the chances of recovery. Also, organizations can be fined if compliance issues are found such as EU citizen data breach should be reported within 72 hours.
FAQs
What is ransomware in simple words?
Ransomware is a malicious application that makes your files unusable and demands for ransom (money) to make them usable again.
What is ransomware and what does it do?
Ransomware is a Malicious application created by hackers. It does lock your files, databases, and applications through encryption.
What is a real example of ransomware?
An employee at a trucking software company clicked on a malicious link that seems like an MS attachment (Ransomware) was downloaded, once executed by the user, all the files were given strange extensions such as “Encryption”
Why it is called ransomware?
It is a type of a malware which demands money to solve the issue cause by it. This money is called ransom which is why cybersecurity industry named it after Ransomware.
Is ransomware a hacker?
No, Ransomware is a malicious Program created by the hacker (malicious actor).
Is ransomware good or bad?
Bad, because it is a malicious software meant to damage the user’s valuable digital assets.
Is ransomware a virus or anti-virus?
Ransomware is a Virus that encrypts your sensitive data on the system.
What are three types of ransomware?
Crypto, Locker, Scareware, Leakware
What’s the difference between a virus and ransomware?
Virus is a malicious program that can modify or delete your data. A malicious program demands for money by locking the access to the system is defined as a ransomware.
Is Trojan a ransomware?
Trojan is not a ransomware. Trojan is a malicious program that looks like a legitimate program, once it is installed on the user’s system, it can steal or modify your data.



